992
Secret room 40
In wartime, to communicate using secure communications. And the interception of messages transmitted to the subsequent decoding - played an important role in the confrontation states. Brilliant Bletchley Park cryptographers have done a tremendous job and have significantly influenced the course of the Second World War. They gained international fame, forever remembering their names in the history of cryptography. But deciphering messages also dealt with during the First World War. In Britain, there decryption organization called Room 40 (Eng. Room 40) which is engaged in intercepting and deciphering German messages.
Room 40 was also known as SB 40 (Old building) and is a division of leading UK cryptographic organ of the First World War - the British Admiralty. He formed an organization in October 1914, shortly after the war began. The name of the room 40 got through the room number in the old building of the Admiralty, where she was. Most of the period of existence of this organization was a Bureau for analysis and deciphering cryptograms. Her staff was deciphered about 15 000 German messages.

Creating Rooms 40B 1911 Communication Committee of Imperial Defence Department, it was decided - in the event of war with Germany must immediately destroy German U-way communication. On the morning of August 5, 1914 cable ship «Alert» determined the cut 5 of the German transatlantic cables that reached the English Channel. Shortly thereafter, 6 cables, which ran between Britain and Germany, were also cut off. As a result, increased the flow of messages transmitted over the radio. To hide their content used codes and ciphers. But to decrypt such messages nor Britain nor Germany existed respective organizations. Messages that could intercept were sent to the intelligence department of the Admiralty, which in 1913 led by Rear Admiral Henry Oliver. But there also were not employees, able to crack the code. Then Oliver turned to his friend the engineer, with experience in radio, Sir Alfred Ewing and asked him to form a group to decrypt messages.

Sir James Alfred Ewing (1855 - 1935 gg.) - Scottish physicist and engineer, known for his work in the field of the magnetic properties of metals. In 1879 he constructed a seismograph, close to the modern. Being a close friend of Charles Parsons, Ewing helped him in the development of the steam engine. In 1897 he took part in the sea trials of the experimental vessel turbines, developing very fast at the time speed (35 knots).
Ewing zealously took up the study of cryptographic material stored in the British Museum Library. Then he began to study the code at the city central post office, where copies of the commercial code books stored. Parallel to this, Ewing began to assemble a team, an introduction to the activity of four teachers Naval College Osborne and Dartmouth. These were his friends, perfectly owning the German language. Together they gathered in Ewing's office, studying incomprehensible string of letters and numbers, with only a very general idea of where to start for the opening codes.
By the middle of the autumn of 1914 the number of employees increased significantly Ewing's group, they are not placed in his office. It took more than a good-sized and technically equipped room. As a result, formed a team of cryptanalysts moved to the old building of the Admiralty and became known as the Room of 40. She was a good location - away from the most crowded spaces Admiralty and close enough to the operations department. Ewing became director of Rooms 40, and his deputy was appointed cryptographer Alistair Denniston.

Alistair Guthrie Denniston (1881- 1961 gg.) - The British cryptographer, the first director of the security services "Government Communications Centre", who held the position in 1919 -1942 gg
. All activities Rooms 40 held in strict confidence and only a very few officers in the Admiralty and the ships of the English Navy knew of its existence. The ability to read the radio reports of German Navy officers gave more information about the operations and intentions of the fleet of Admiral Scheer, than there was in any other division of the Royal Navy. Intercepted and decoded text messages sent to any of the small group of officers dedicated to operational management of staff of naval forces of Britain. To review all the messages and their interpretation in terms of information picked Herbert Hope, who had previously worked on the route of movement of enemy ships. Hope was placed in a small room, where he tried to understand the meaning of the messages and make useful observations. But full access to the information he received only later, after a chance meeting with the First Lord of the Admiralty Sir John Arbuthnot Fisher.
A significant disadvantage of the organization of the 40 rooms was that it could not act as an operational intelligence center. No messages processed by room 40, could not be sent without the personal approval Oliver (except for certain approved First Lord of the Admiralty, or Lord). The members of this organization knew that they decrypted information is not used in full because of the extreme secrecy and restrictions to share its intelligence with other departments. As already mentioned, the chain of command transfer prepared in Room 40 and it is only well-understandable information entrusted to a small group of officers. But they did not have any special knowledge or skills relevant to always correctly interpret the importance of the transcripts, and optimally manage their further fate.
In 1917 we came some changes - Room 40 has ceased to supply raw Intelligence information and start to transfer all the actual materials in the form of thoughtful assessments of intentions and the nature of the movements of ships Germans.
Capture codebook SKMV 1914 Russia gave the UK 'Book of the Imperial Navy signals »(Signalbuch der Kaiserlich Marine, SKM), which was captured by Russian sailors in the German cruiser" Magdeburg ". British copy of the book was presented in person to the first Lord of the Admiralty Winston Leonard Churchill.
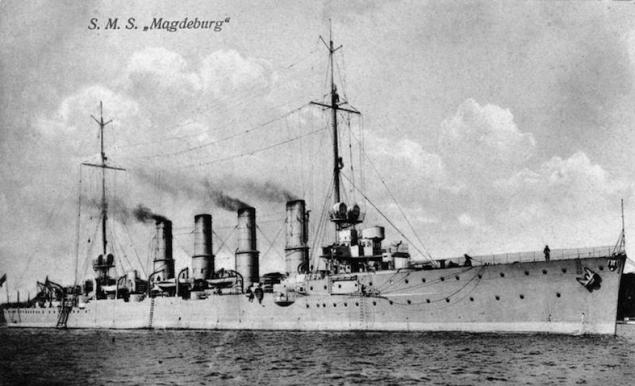
cruiser "Magdeburg»
Getting SKM was the first breakthrough for staff rooms 40. To use a needed book was current key. There have also been restored Card Baltic, logbook and war diaries.
Sheets of SKM Books (More can be found here):




By itself, SKM was incomplete because messages usually encrypted and coded. German expert Naval Intelligence Division of CJ. E. Rotter was instructed to use the SKM to interpret the intercepted cipher, most of which were produced in deciphering meaningless. The beginning of solving the problem was a series of messages transmitted from the transmitter German Norddeich. They were numbered sequentially and decrypted once the intelligence reports on the whereabouts of the Allied ships. In fact, the code has been cracked twice, because after a few days it changed to the general procedure for the interpretation of messages was determined. Encryption consists of a conventional table replacing one letter in all other messages.
The German navy used the SKM, the code at the time of important activities. Transfer between the courts took place in the form of simple combinations of signal flags or lamps flashes. SKM 34000 contains instructions, each of which was represented by a different group of three letters. Signals used four characters that are not in the usual Morse code (because of what cryptanalysts faced difficulties). But over time, cryptographers of Room 40 have learned to recognize and use a standardized method of recording signals. Ships determined group of three letters, starting with the beta character. Messages that are not covered by the pre-defined list can be registered using a lookup table to individual letters.
The huge size of the book was one of the reasons why it can not be easily changed. Code continued to be used until the summer of 1916. The current substitution table that was used to encrypt, was generated by a mechanical device thumbnail and compartments for letters. Orders of the key change was sent to radio. Confusion occurred in the period of change has led to the fact that messages are sent using a new cipher, and then repeated with the old. key changes do not occur often, only 6 times from March to the end of 1915, but since 1916 they frequent.
Capture codebook HVBNe less important code, which was used by the German navy, was contained in the book «Handelsverkehrsbuch» ( HVB). She got a copy to the British after the successful capture of the German-Australian steamer "Hobart" in Australia August 11, 1914. The German navy used the code book from HVB encryption to communicate with merchant ships, as well as in high seas fleet.
Sheets of HVB Books (More can be found here):
HVB was issued in 1913 to all warships with radio, naval command and coast stations, as well as sold at the main offices of eighteen German shipping companies for the issue of their own vessels to the radio. The code has been used 450,000 possible permutations of four letters. This gave an alternative view of the same value by adding an extra ten letters grouped for use in communications. The most common code used patrol boats. It is also used for normal tasks, such as the entrance and exit ports. Submarines use the code with more complex key.
In 1914, of the radio communications, it became known that the German intelligence learned of the passing HVB books to the British. But that less code was replaced only in 1916 on «Allgemeinefunkspruchbuch» (AFB), along with a new coding method. The British got a good idea of the new method of encryption to the test signals, before being introduced to the real messages. At this time, more organizations have received the new code. Compared with its predecessor from AFB was more groups, but with only two letters. The first captured a copy taken from the downed «Zeppelin», while others have withdrawn from the sunken submarine.
Sheets of AFB Books (More can be found here):



Capture codebook VBV 1914 in Room 40 got a copy of the third codebook Germany under the name «Verkehrsbuch» (VB). It was restored after the sinking of the German destroyers S119 in the battle of Texel. The commander jettisoned secret documents in a lead box and it was believed that they lost. But a month passed, and pulled out a box to decrypt the staff rooms 40. In the box is a copy of «Verkehrsbuch», which was used by the commander of the German fleet. The code was 100000 group of 5 digits, each having a special meaning. It was used for encryption of telegrams sent abroad for warships and naval attaches, embassies and consulates.
Code from VB has provided access to the means of communication between the naval attache in Berlin, Madrid, Washington, Buenos Aires, Beijing and Constantinople.

decrypted command Rooms 40 Journal of the German submarine U20 (located in the National Archives in London)

Room 40 regularly intercepts the message and have very precise information about the position of the German ships. Yet British ships received clear instructions indicating the use of radio as little as possible and at the lowest frequency
Telegram TsimmermanaNaibolee significant achievement in the history of Rooms 40 naval battles began deciphering the Zimmermann Telegram. It was dated January 19, 1917 and was directed by the Ministry of Foreign Affairs of Germany to Ambassador Heinrich von Eckardt in Mexico.
Under the guise of a diplomatic telegram messages on the radio and telegraph through neutral countries: Sweden and USA. Germany had to use the telegraph British and American channels. The Germans were forced to take such a risk, because it does not have direct access to the telegraph western hemisphere, as the British cut their transatlantic cables and transmitting stations destroyed.

Zimmermann Telegram
The text of the telegram was reported that German Foreign Minister Arthur Zimmermann suggested Mexico, United States (Arizona, New Mexico and Texas), if she will take part in the war as an ally of Germany. The British government understands the value of the communication. But it was necessary to solve two problems. First, explain to Americans how telegram was received, without disclosing the fact that British intelligence checks pouches neutral countries. Second, to give a public explanation of how the telegram was deciphered, but so that Germany does not suspect anything (that codes hacked).
The first problem was solved when the British gained ciphertext telegrams from telegraph office in Mexico. German Ambassador conveyed a message from Washington to Mexico commercial telegraph, so the Mexican telegraph department obtained a copy of the encrypted text. British agent got this copy and handed Americans. The text has been encrypted code 13040, a model of which Britain acquired back in Mesopotamia. The Germans scrambled their messages using a conventional algorithm of the Ministry of Foreign Affairs and a number of key 0075, which experts Rooms 40 already partially cracked. The algorithm includes the replacement of the words (encoding) as well as the replacement of letters (encryption). It is common practice that in Germany and used in another encryption method - cipher ADFGVX
. According to the "official" version of the decrypted text of the telegram was stolen by the British in Mexico and handed over to the Americans. And April 6, 1917 the United States declared war on Germany.
Code ADFGVXRazrabotchik font - liaison officer Colonel Fritz Nebel. The peculiarity of this cipher was the fact that it was built at the junction of the base of operations of replacement and rearrangement. Item part corresponding to the replacement, based on Polybius square.
The cryptogram containing only the letter «A», «D», «F», «G» and «X» (from here and the name of the cipher). The choice of these letters was not accidental. If you present them in the form of dots and dashes of Morse code, they will be significantly different from each other. In fact - it was Polybius square, which in a certain order fit the Latin alphabet. Since 1918, he added the letter «V», complicating and increasing the encryption cipher grid up to 36 characters. This has allowed to include in the plaintext digits from 0 to 9, besides the letters I and J become encrypted differently.
At the heart of the cipher was 6 letters: «A», «D», «F», «G», «V» and «X». Table shifrozamen for ADFGX was a 5 x 5 matrix, and for ADFGVX - 6 x 6 rows and columns are denoted by the letter, included in the name of the cipher. Arrangement of elements in the table are part of the key.

Shifrozamena for the letter of the original text composed of letters denoting the row and column at the intersection where it was.

In the second stage to perform a set of permutations resulting shifrozamen fit line by line from top to bottom in the table. The table was strictly defined number of columns and conform to the number of letters in the keyword. Column numbering or previously agreed between the parties or is aligned with the keyword letter in the alphabet. This created a new table with the keyword in the top line.
For example - consider the message in English: «attack will begin in 11 am». We can take the word «SECRET» as the key. But as a rule, use longer keywords or phrases.

The table columns are sorted in alphabetical order.

Further letters were discharged from the columns according to their numbering, and the reading took place on the columns, and the letters were combined into five-letter groups. Thus, the final form of the ciphertext looked:
G X F G F F D F F A D D F A G F X D F A D X V F A F G F D D X X V F A X V D A G A X
To restore the original text required to follow the steps the reverse encryption. Column sequence could lead to the original order, using a keyword. Knowing the locations of characters in the source table has helped to decipher the text.
The text of the telegram:
We intend to begin on 1 February ruthless submarine warfare. In spite of that, we try to keep the US in the state of neutrality. However, in case of failure, we will offer Mexico: together to wage war and make peace together. С нашей стороны мы окажем Мексике финансовую помощь и заверим, что по окончании войны она получит обратно утраченные ею территории Техаса, Новой Мексики и Аризоны. Мы поручаем вам выработать детали этого соглашения. Вы немедленно и совершенно секретно предупредите президента Каррансу, как только объявление войны между нами и США станет совершившимся фактом. Добавьте, что президент Мексики может по своей инициативе сообщить японскому послу, что Японии было бы очень выгодно немедленно присоединиться к нашему союзу. Обратите внимание президента на тот факт, что мы впредь в полной мере используем наши подводные силы, что заставит Англию подписать мир в ближайшие месяцы.Завершение историиГерманское командование приступило к корректировке своих шифров лишь с 1916 года, ежемесячно меняя коды (а позднее даже ежесуточно). Но при этом принцип шифрования остался прежним. И к этому времени специалисты из Комнаты 40 уже совсем освоились с немецкой шифровальной системой, ускорив процесс дешифровки сообщения. Иногда содержание немецких радиограмм в Лондоне узнавали раньше их адресата.

Старое Адмиралтейство
В 1919 году Комнату 40 расформировали и на ее базе, а также на базе криптографического подразделения разведки британской армии MI1b (англ. Military Intelligence, Section 1) была сформирована Правительственная школа кодирования и шифрования (GC&CS). Во время Второй мировой войны эта школа размещалась в Блетчли-Парке и впоследствии стала независимой от военной разведки службой радиоэлектронной разведки. В 1946 году она была переименована в Центр правительственной связи (англ. Government Communications Headquarters, GCHQ), а с 1951 года по 1952 год перемещена в Челтнем. Но фактическая комната 40 до сих пор располагается на первом этаже в Здании Адмиралтейства на Уайтхолл в Лондоне.
Источник: geektimes.ru/company/ua-hosting/blog/277056/
Room 40 was also known as SB 40 (Old building) and is a division of leading UK cryptographic organ of the First World War - the British Admiralty. He formed an organization in October 1914, shortly after the war began. The name of the room 40 got through the room number in the old building of the Admiralty, where she was. Most of the period of existence of this organization was a Bureau for analysis and deciphering cryptograms. Her staff was deciphered about 15 000 German messages.

Creating Rooms 40B 1911 Communication Committee of Imperial Defence Department, it was decided - in the event of war with Germany must immediately destroy German U-way communication. On the morning of August 5, 1914 cable ship «Alert» determined the cut 5 of the German transatlantic cables that reached the English Channel. Shortly thereafter, 6 cables, which ran between Britain and Germany, were also cut off. As a result, increased the flow of messages transmitted over the radio. To hide their content used codes and ciphers. But to decrypt such messages nor Britain nor Germany existed respective organizations. Messages that could intercept were sent to the intelligence department of the Admiralty, which in 1913 led by Rear Admiral Henry Oliver. But there also were not employees, able to crack the code. Then Oliver turned to his friend the engineer, with experience in radio, Sir Alfred Ewing and asked him to form a group to decrypt messages.

Sir James Alfred Ewing (1855 - 1935 gg.) - Scottish physicist and engineer, known for his work in the field of the magnetic properties of metals. In 1879 he constructed a seismograph, close to the modern. Being a close friend of Charles Parsons, Ewing helped him in the development of the steam engine. In 1897 he took part in the sea trials of the experimental vessel turbines, developing very fast at the time speed (35 knots).
Ewing zealously took up the study of cryptographic material stored in the British Museum Library. Then he began to study the code at the city central post office, where copies of the commercial code books stored. Parallel to this, Ewing began to assemble a team, an introduction to the activity of four teachers Naval College Osborne and Dartmouth. These were his friends, perfectly owning the German language. Together they gathered in Ewing's office, studying incomprehensible string of letters and numbers, with only a very general idea of where to start for the opening codes.
By the middle of the autumn of 1914 the number of employees increased significantly Ewing's group, they are not placed in his office. It took more than a good-sized and technically equipped room. As a result, formed a team of cryptanalysts moved to the old building of the Admiralty and became known as the Room of 40. She was a good location - away from the most crowded spaces Admiralty and close enough to the operations department. Ewing became director of Rooms 40, and his deputy was appointed cryptographer Alistair Denniston.

Alistair Guthrie Denniston (1881- 1961 gg.) - The British cryptographer, the first director of the security services "Government Communications Centre", who held the position in 1919 -1942 gg
. All activities Rooms 40 held in strict confidence and only a very few officers in the Admiralty and the ships of the English Navy knew of its existence. The ability to read the radio reports of German Navy officers gave more information about the operations and intentions of the fleet of Admiral Scheer, than there was in any other division of the Royal Navy. Intercepted and decoded text messages sent to any of the small group of officers dedicated to operational management of staff of naval forces of Britain. To review all the messages and their interpretation in terms of information picked Herbert Hope, who had previously worked on the route of movement of enemy ships. Hope was placed in a small room, where he tried to understand the meaning of the messages and make useful observations. But full access to the information he received only later, after a chance meeting with the First Lord of the Admiralty Sir John Arbuthnot Fisher.
A significant disadvantage of the organization of the 40 rooms was that it could not act as an operational intelligence center. No messages processed by room 40, could not be sent without the personal approval Oliver (except for certain approved First Lord of the Admiralty, or Lord). The members of this organization knew that they decrypted information is not used in full because of the extreme secrecy and restrictions to share its intelligence with other departments. As already mentioned, the chain of command transfer prepared in Room 40 and it is only well-understandable information entrusted to a small group of officers. But they did not have any special knowledge or skills relevant to always correctly interpret the importance of the transcripts, and optimally manage their further fate.
In 1917 we came some changes - Room 40 has ceased to supply raw Intelligence information and start to transfer all the actual materials in the form of thoughtful assessments of intentions and the nature of the movements of ships Germans.
Capture codebook SKMV 1914 Russia gave the UK 'Book of the Imperial Navy signals »(Signalbuch der Kaiserlich Marine, SKM), which was captured by Russian sailors in the German cruiser" Magdeburg ". British copy of the book was presented in person to the first Lord of the Admiralty Winston Leonard Churchill.

cruiser "Magdeburg»
Getting SKM was the first breakthrough for staff rooms 40. To use a needed book was current key. There have also been restored Card Baltic, logbook and war diaries.
Sheets of SKM Books (More can be found here):




By itself, SKM was incomplete because messages usually encrypted and coded. German expert Naval Intelligence Division of CJ. E. Rotter was instructed to use the SKM to interpret the intercepted cipher, most of which were produced in deciphering meaningless. The beginning of solving the problem was a series of messages transmitted from the transmitter German Norddeich. They were numbered sequentially and decrypted once the intelligence reports on the whereabouts of the Allied ships. In fact, the code has been cracked twice, because after a few days it changed to the general procedure for the interpretation of messages was determined. Encryption consists of a conventional table replacing one letter in all other messages.
The German navy used the SKM, the code at the time of important activities. Transfer between the courts took place in the form of simple combinations of signal flags or lamps flashes. SKM 34000 contains instructions, each of which was represented by a different group of three letters. Signals used four characters that are not in the usual Morse code (because of what cryptanalysts faced difficulties). But over time, cryptographers of Room 40 have learned to recognize and use a standardized method of recording signals. Ships determined group of three letters, starting with the beta character. Messages that are not covered by the pre-defined list can be registered using a lookup table to individual letters.
The huge size of the book was one of the reasons why it can not be easily changed. Code continued to be used until the summer of 1916. The current substitution table that was used to encrypt, was generated by a mechanical device thumbnail and compartments for letters. Orders of the key change was sent to radio. Confusion occurred in the period of change has led to the fact that messages are sent using a new cipher, and then repeated with the old. key changes do not occur often, only 6 times from March to the end of 1915, but since 1916 they frequent.
Capture codebook HVBNe less important code, which was used by the German navy, was contained in the book «Handelsverkehrsbuch» ( HVB). She got a copy to the British after the successful capture of the German-Australian steamer "Hobart" in Australia August 11, 1914. The German navy used the code book from HVB encryption to communicate with merchant ships, as well as in high seas fleet.
Sheets of HVB Books (More can be found here):


HVB was issued in 1913 to all warships with radio, naval command and coast stations, as well as sold at the main offices of eighteen German shipping companies for the issue of their own vessels to the radio. The code has been used 450,000 possible permutations of four letters. This gave an alternative view of the same value by adding an extra ten letters grouped for use in communications. The most common code used patrol boats. It is also used for normal tasks, such as the entrance and exit ports. Submarines use the code with more complex key.
In 1914, of the radio communications, it became known that the German intelligence learned of the passing HVB books to the British. But that less code was replaced only in 1916 on «Allgemeinefunkspruchbuch» (AFB), along with a new coding method. The British got a good idea of the new method of encryption to the test signals, before being introduced to the real messages. At this time, more organizations have received the new code. Compared with its predecessor from AFB was more groups, but with only two letters. The first captured a copy taken from the downed «Zeppelin», while others have withdrawn from the sunken submarine.
Sheets of AFB Books (More can be found here):



Capture codebook VBV 1914 in Room 40 got a copy of the third codebook Germany under the name «Verkehrsbuch» (VB). It was restored after the sinking of the German destroyers S119 in the battle of Texel. The commander jettisoned secret documents in a lead box and it was believed that they lost. But a month passed, and pulled out a box to decrypt the staff rooms 40. In the box is a copy of «Verkehrsbuch», which was used by the commander of the German fleet. The code was 100000 group of 5 digits, each having a special meaning. It was used for encryption of telegrams sent abroad for warships and naval attaches, embassies and consulates.
Code from VB has provided access to the means of communication between the naval attache in Berlin, Madrid, Washington, Buenos Aires, Beijing and Constantinople.

decrypted command Rooms 40 Journal of the German submarine U20 (located in the National Archives in London)

Room 40 regularly intercepts the message and have very precise information about the position of the German ships. Yet British ships received clear instructions indicating the use of radio as little as possible and at the lowest frequency
Telegram TsimmermanaNaibolee significant achievement in the history of Rooms 40 naval battles began deciphering the Zimmermann Telegram. It was dated January 19, 1917 and was directed by the Ministry of Foreign Affairs of Germany to Ambassador Heinrich von Eckardt in Mexico.
Under the guise of a diplomatic telegram messages on the radio and telegraph through neutral countries: Sweden and USA. Germany had to use the telegraph British and American channels. The Germans were forced to take such a risk, because it does not have direct access to the telegraph western hemisphere, as the British cut their transatlantic cables and transmitting stations destroyed.

Zimmermann Telegram
The text of the telegram was reported that German Foreign Minister Arthur Zimmermann suggested Mexico, United States (Arizona, New Mexico and Texas), if she will take part in the war as an ally of Germany. The British government understands the value of the communication. But it was necessary to solve two problems. First, explain to Americans how telegram was received, without disclosing the fact that British intelligence checks pouches neutral countries. Second, to give a public explanation of how the telegram was deciphered, but so that Germany does not suspect anything (that codes hacked).
The first problem was solved when the British gained ciphertext telegrams from telegraph office in Mexico. German Ambassador conveyed a message from Washington to Mexico commercial telegraph, so the Mexican telegraph department obtained a copy of the encrypted text. British agent got this copy and handed Americans. The text has been encrypted code 13040, a model of which Britain acquired back in Mesopotamia. The Germans scrambled their messages using a conventional algorithm of the Ministry of Foreign Affairs and a number of key 0075, which experts Rooms 40 already partially cracked. The algorithm includes the replacement of the words (encoding) as well as the replacement of letters (encryption). It is common practice that in Germany and used in another encryption method - cipher ADFGVX
. According to the "official" version of the decrypted text of the telegram was stolen by the British in Mexico and handed over to the Americans. And April 6, 1917 the United States declared war on Germany.
Code ADFGVXRazrabotchik font - liaison officer Colonel Fritz Nebel. The peculiarity of this cipher was the fact that it was built at the junction of the base of operations of replacement and rearrangement. Item part corresponding to the replacement, based on Polybius square.
The cryptogram containing only the letter «A», «D», «F», «G» and «X» (from here and the name of the cipher). The choice of these letters was not accidental. If you present them in the form of dots and dashes of Morse code, they will be significantly different from each other. In fact - it was Polybius square, which in a certain order fit the Latin alphabet. Since 1918, he added the letter «V», complicating and increasing the encryption cipher grid up to 36 characters. This has allowed to include in the plaintext digits from 0 to 9, besides the letters I and J become encrypted differently.
At the heart of the cipher was 6 letters: «A», «D», «F», «G», «V» and «X». Table shifrozamen for ADFGX was a 5 x 5 matrix, and for ADFGVX - 6 x 6 rows and columns are denoted by the letter, included in the name of the cipher. Arrangement of elements in the table are part of the key.

Shifrozamena for the letter of the original text composed of letters denoting the row and column at the intersection where it was.

In the second stage to perform a set of permutations resulting shifrozamen fit line by line from top to bottom in the table. The table was strictly defined number of columns and conform to the number of letters in the keyword. Column numbering or previously agreed between the parties or is aligned with the keyword letter in the alphabet. This created a new table with the keyword in the top line.
For example - consider the message in English: «attack will begin in 11 am». We can take the word «SECRET» as the key. But as a rule, use longer keywords or phrases.

The table columns are sorted in alphabetical order.

Further letters were discharged from the columns according to their numbering, and the reading took place on the columns, and the letters were combined into five-letter groups. Thus, the final form of the ciphertext looked:
G X F G F F D F F A D D F A G F X D F A D X V F A F G F D D X X V F A X V D A G A X
To restore the original text required to follow the steps the reverse encryption. Column sequence could lead to the original order, using a keyword. Knowing the locations of characters in the source table has helped to decipher the text.
The text of the telegram:
We intend to begin on 1 February ruthless submarine warfare. In spite of that, we try to keep the US in the state of neutrality. However, in case of failure, we will offer Mexico: together to wage war and make peace together. С нашей стороны мы окажем Мексике финансовую помощь и заверим, что по окончании войны она получит обратно утраченные ею территории Техаса, Новой Мексики и Аризоны. Мы поручаем вам выработать детали этого соглашения. Вы немедленно и совершенно секретно предупредите президента Каррансу, как только объявление войны между нами и США станет совершившимся фактом. Добавьте, что президент Мексики может по своей инициативе сообщить японскому послу, что Японии было бы очень выгодно немедленно присоединиться к нашему союзу. Обратите внимание президента на тот факт, что мы впредь в полной мере используем наши подводные силы, что заставит Англию подписать мир в ближайшие месяцы.Завершение историиГерманское командование приступило к корректировке своих шифров лишь с 1916 года, ежемесячно меняя коды (а позднее даже ежесуточно). Но при этом принцип шифрования остался прежним. И к этому времени специалисты из Комнаты 40 уже совсем освоились с немецкой шифровальной системой, ускорив процесс дешифровки сообщения. Иногда содержание немецких радиограмм в Лондоне узнавали раньше их адресата.

Старое Адмиралтейство
В 1919 году Комнату 40 расформировали и на ее базе, а также на базе криптографического подразделения разведки британской армии MI1b (англ. Military Intelligence, Section 1) была сформирована Правительственная школа кодирования и шифрования (GC&CS). Во время Второй мировой войны эта школа размещалась в Блетчли-Парке и впоследствии стала независимой от военной разведки службой радиоэлектронной разведки. В 1946 году она была переименована в Центр правительственной связи (англ. Government Communications Headquarters, GCHQ), а с 1951 года по 1952 год перемещена в Челтнем. Но фактическая комната 40 до сих пор располагается на первом этаже в Здании Адмиралтейства на Уайтхолл в Лондоне.
Источник: geektimes.ru/company/ua-hosting/blog/277056/