1351
10 of the most interesting facts about codes and ciphers

The need to hide the contents of important messages has existed for thousands of years. Over time, people found more and more sophisticated ways of encoding messages as simple ways of coding are decoded with greater ease. Today in the world there are thousands of ways to conceal messages, but in this review we consider only ten of them.
1. Steganografiya

Steganography is more ancient than the codes and ciphers, and usually it is called cryptography, the art of covert recording. For example, a message can be written on paper coated with wax, and a messenger has to swallow it and thus ensure secrecy and the right moment to burp to a message can be read. Another way is to tattoo messages on the shaved head of messenger, then it is necessary to wait until the hair grow again to hide the message. The best way to cryptography - is to use ordinary objects to hide the message. In England, it was a popular method of cryptography, which is used for the usual paper with tiny dots under the letters on the first page, which indicated what letters should be read to get the message. Some people can compose a message using the first letter of each word in any text or using invisible ink. Competing countries can shrink the text so that an entire page of text becomes the size of a pixel that is invisible to prying eyes. Steganography is best used in conjunction with the code or cipher, as there is a risk that the secret message can be found.
2. ROT1

This cipher is familiar to many children. The key to the code is very simple: each letter of the alphabet is replaced with the subsequent letter, however, A is replaced by B, B is replaced by B, and so on. «ROT1» literally means "to rotate at 1 forward the letter in alphabetical order." The phrase, "I know everything" will become a secret phrase "A gtё Kobyay." This code is intended for entertainment, because it is easy to understand and use, and just as easy to decipher, even if the key is used in the reverse direction.
3. Perestanovka

The adjustable cipher letters rearranged using some set of rules or keys. For example, words can be written in the opposite direction, so that the phrase "good to see you" turns the phrase "gift tediv CAB." Another key permutation is a permutation of each pair of letters, so that the previous message becomes "ar bg de sa Bb ones." These ciphers are used to send confidential messages during the First World War and the American Civil War. At first glance, it seems that the complex rules of transposition ciphers can make these very difficult. However, many encrypted messages can be decrypted using anagrams or advanced computer algorithms that sorted out thousands of possible permutations of keys.
4. Morse code (Morse)

Despite its name, Morse code is not the code - this code. Each letter of the alphabet, numbers 0 to 9 and certain punctuation characters are replaced by a sequence of short and long beeps, which are often called "dot and dash." A becomes «• -«, B becomes «- • • •» and so on. Unlike most other ciphers, Morse code is not used to hide messages. Morse code began to be widely used with the invention of the telegraph by Samuel Morse. It was the first widely used electrical device for transmitting messages over long distances. The telegraph revolutionized the media and you can immediately send messages about events that have taken place in one country, all over the world. Morse code has changed the nature of war, allowing to provide instant communication with the troops at a great distance.
5. Code Tsezarya
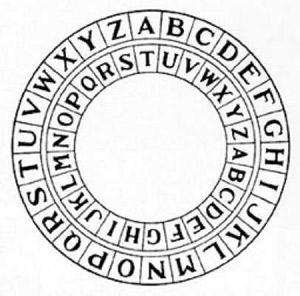
Caesar cipher (sliding), so called because it was used by Julius Caesar. The code is actually from 33 different codes (the number of codes varies according to the alphabet of the language used), one for each letter of the alphabet. «ROT1» is just one of those ciphers. The man had to know what the Caesar cipher used to decrypt the message. If you use the code E, then A becomes E, B becomes F, B becomes H, and so on through the alphabet. If you use code U, then A becomes Yu, B becomes H, B becomes A, and so on. This algorithm is the basis for many of the more complex codes, but by itself does not provide protection for confidentiality of messages, since checking 33 different cipher keys takes relatively little time.
6. monoalphabetic zamena
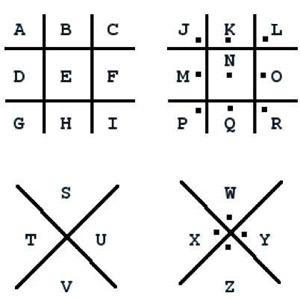
ROT1, Caesar cipher Morse code and belong to the same type - monoalphabetic replacement, which means that each letter of the alphabet is replaced in accordance with the key, another letter or symbol. In fact, they are easy to decipher, even without knowing the key. The most commonly used letter in the English language is the letter E. Thus, in many monoalphabetic ciphers, the most common letter or symbol will also be E (approx. Translator. - In the Russian language the most common - is the letter O). The second most common letter in the English language - a T, and the third is a letter, and, therefore, these two letters can also be specified for decryption. From this point of view, people can decrypt the message using the frequency of English letters, or it may look almost complete words such as «T_E», which is the most likely way is «THE».
7. Code Vizhenera
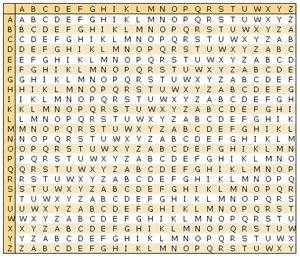
This algorithm is more complex than monoalfavitnyya replacement. His key words are such words such as «CHAIR». The first letter of the message with the keyword «CHAIR» will be encoded with the alphabetical codes C, the second letter alphabetical codes H and so it goes to the last letter of the keyword. Keyword consists of only five letters, so for the sixth letter of the message will again be used by an alphabetical code C. long time it was thought that it is impossible to crack the Vigenère cipher. To decrypt it, first of all, we must find the length of the keyword. If the keyword is made up of five letters, the letters with numbers 1, 6, 11, 16, 21, and so on. D. Will match the first letter of the keyword, and the analysis of the frequency of letters will enable to decrypt the message. Dekoderovschik then proceeds to letters 2, 7, 12, 17, and so on. If a keyword is, actually consists of five letters, the message will be easy to decipher. If not, you need to find another keyword, and then repeat the process.
8. Original kod

The original code is replaced every word the code word or number in accordance with the key. Because the message may be many words, the key is usually stored in the codebook. Dekoderovschik can see the English word and find the corresponding code word. Since short messages difficult to decipher by analyzing the frequency of the letters, the code must be extremely long, otherwise the analysis of the frequency of use of speech becomes useful in decoding. For this reason code harder to decipher than ciphers. Many countries use such options code that every day a new code used to prevent decoding by means of frequency analysis of the words. For everyday life, however, the use of code - a rather tedious process and the codebook rather cumbersome. If a book is stolen code, the code is already unsafe and you need to create a new code, and it requires a huge amount of time and effort. Codes are mainly useful for the rich and powerful, who can delegate the work to others.
9. Code Enigma

Enigma Code, which was very difficult cipher used by the Germans during World War II. To do this, use the machine Enigma, which is very similar to a typewriter, when you click on a particular letter on the screen light up the letter cipher. The machine had a few wheels that have been associated with the letters of wires to determine which cipher letter will be displayed. All Enigma machines were identical, and the initial configuration of the wheels was the key to encrypt the message. To complicate the process, the wheel must be rotated after a certain number of letters were printed. The German command every day issued a list of initial configuration of the wheels to be used in encryption, so all German commanders used the same configuration, and can decrypt messages to each other. Even when the Allies got hold of a copy machine, they still could not decipher the message, because the machine gave out hundreds of trillions of possible initial configurations of the wheels. Enigma code was cracked by Polish craftsmen and finally deciphered by the British, who used ingenuity and computers. Knowledge of German communication systems give a significant advantage to the Allies during the war, and the process of cracking the Enigma code, allowed to create a first prototype of a computer.
10. Cryptography open klyuchami
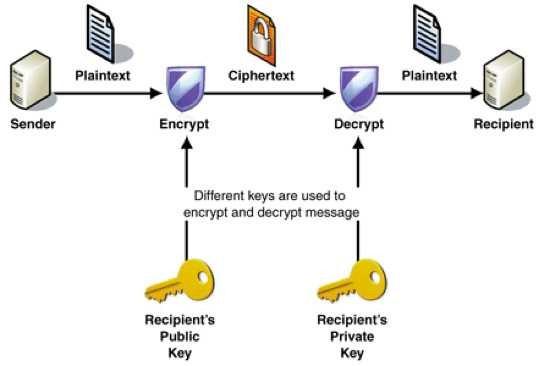
It is the most modern cipher, and it has several options. This code, which is used worldwide, and has two keys: one public and one private. Public Key - a large number, available to all. Key is so complex because there may be obtained by dividing only two integers (except 1 and the number itself). These two numbers is the private key, and if they multiply, get the public key. For example, the public key can be in 1961, therefore, the private key - it's 37 and 53. The public key is used to encrypt a message, and the message can not be decrypted without the private key. When you send personal information to the bank, or if your bank card is processed by the machine, the data is encrypted in this way, and only the bank with his private key can access them. The reason why this method is as secure, is mathematically very hard to find the divisors of large numbers. To improve security before 2007, the company «RSA Laboratories» paid money to anyone who could find a divisor for two numbers that it offers. This is a relatively easy example, which cost $ 1,000, you are encouraged to find two 50-digit numbers for the divider: 15226050279225333605356183781326374 29718068114961380688657908494580 12296325895289765400350692006139 (moved).
via factroom.ru
Bloboll - a game of hockey lips
Klein bottle has no edges and do not apply to it the concept of "inside" and "outside"