215
Where do hackers get our passwords and bank card numbers?
The Internet, smartphones and social networks have become an integral part of our lives. They have greatly simplified the world and taken on most of the daily tasks. We didn’t even have time to look back, as money, entertainment, services and shopping migrated online. Progress is certainly a good thing, but the price of comfort is online security. In order to protect ourselves from hacking, we will tell you about where hackers get our passwords and bank card numbers.

For an experienced hacker, it will not be difficult to hack the page of an ordinary user of any social network. On average, the culture of internet security remains very low. Most people use the same passwords to different sites, click on suspicious links from spam and fundamentally abandon password managers. This leads to the fact that the number of Internet crimes is growing every year.

Some hackers are just having fun, others are looking for profit. Worst of all, when they get to the post office or bank card. In this case, you can lose not only control over the information, but also the funds in the account. Of course, it is in the interests of attackers to hack into a rich person or a large company more often - but this is the mistake: ordinary people think that no one cares about them. This makes their security even more vulnerable.

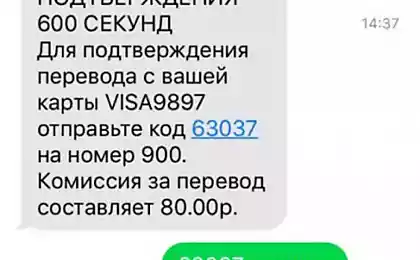
How hackers operate phishing This is a way to lure a user to a fake website, a kind of fishing for a hacker. The site may pose as “real” and offer to enter a password that can be intercepted. In order not to fall for this bait, you need to visit only proven resources. Hackers are also being used. malware Viruses that can be downloaded and installed on your computer by mistake.

To protect yourself, you need to carefully check the downloaded files and try not to go to “doubtful” sites. In addition, it is better not to rely on it and install a quality antivirus. It can protect your computer and make internet access more secure.
737240
First of all, the hackers can simply guessHaving information about the user that is easy to find on social networks. Secondly, they can automatically go through a large number of options, using for this purpose. database Or dictionary attack techniques. People think in a similar way, so in order to come up with a password, it is better to use a special generator. You can find it online again, but it should be a proven resource.

Large sites are protected from password selection, but if you use one password for all sites, then all your information is at risk. Therefore, for everything related to mail, banks and money, it is better to use different, reliable passwords and dual authorization service. By the way, knowing the password from the mailbox, a hacker can go even further and get a card number and even a pin code. Therefore, we recommend using a separate bank card or virtual wallet for online purchases.

Summing up, I would like to note that the fault of everything is banal inattention and carelessness. At first it seems that the Internet is a beautiful world with beautiful pictures, but in fact it can be as dangerous as reality. That's why filter the information correctly on the network and use strong passwords. What methods help you use the internet safely?

For an experienced hacker, it will not be difficult to hack the page of an ordinary user of any social network. On average, the culture of internet security remains very low. Most people use the same passwords to different sites, click on suspicious links from spam and fundamentally abandon password managers. This leads to the fact that the number of Internet crimes is growing every year.

Some hackers are just having fun, others are looking for profit. Worst of all, when they get to the post office or bank card. In this case, you can lose not only control over the information, but also the funds in the account. Of course, it is in the interests of attackers to hack into a rich person or a large company more often - but this is the mistake: ordinary people think that no one cares about them. This makes their security even more vulnerable.

How hackers operate phishing This is a way to lure a user to a fake website, a kind of fishing for a hacker. The site may pose as “real” and offer to enter a password that can be intercepted. In order not to fall for this bait, you need to visit only proven resources. Hackers are also being used. malware Viruses that can be downloaded and installed on your computer by mistake.

To protect yourself, you need to carefully check the downloaded files and try not to go to “doubtful” sites. In addition, it is better not to rely on it and install a quality antivirus. It can protect your computer and make internet access more secure.
737240
First of all, the hackers can simply guessHaving information about the user that is easy to find on social networks. Secondly, they can automatically go through a large number of options, using for this purpose. database Or dictionary attack techniques. People think in a similar way, so in order to come up with a password, it is better to use a special generator. You can find it online again, but it should be a proven resource.

Large sites are protected from password selection, but if you use one password for all sites, then all your information is at risk. Therefore, for everything related to mail, banks and money, it is better to use different, reliable passwords and dual authorization service. By the way, knowing the password from the mailbox, a hacker can go even further and get a card number and even a pin code. Therefore, we recommend using a separate bank card or virtual wallet for online purchases.

Summing up, I would like to note that the fault of everything is banal inattention and carelessness. At first it seems that the Internet is a beautiful world with beautiful pictures, but in fact it can be as dangerous as reality. That's why filter the information correctly on the network and use strong passwords. What methods help you use the internet safely?
What's wrong with washing clothes at forty degrees and above
Why do motorists pour a glass of air conditioning for laundry into the washing tank?