901
How to conduct a secret correspondence in a world where you are constantly being watched: methods Edward Snowden
Part 1
When you pick up the phone and make a call, send SMS, email, post to Facebook or Google Hangouts, others can track what you say, who're talking and where you are. This personal information may be available not only to the service provider who acts as a mediator in your conversation, but telecommunications companies, which provides access to the Internet, the intelligence services and law enforcement agencies, and even a few teenagers that can track your actions in a Wi-Fi network using the application Wireshark.
However, if you take the necessary steps to protect your information, you will be able to send secret and anonymous online messages. In this article I will in detail tell about how to do it. We will consider the methods by which two and a half years ago, I used the informant and ex-NSA employee Edward Snowden to contact me. In other words, I will show you how to create an anonymous account for online correspondence and exchange of messages using encryption Protocol called Off-the-Record Messaging, or OTR.
If you don't want to read the entire article, you can skip to the section where the phases described how to create account on Mac OS X, Windows, Linux and Android. When you have enough time, go back to the beginning and read the important points that go to these sections.

First, you need to make sure that you are using encryption between the end-users [eng. end-to-end encryption]. In this case, the message is encrypted on one end – say, on a smartphone – and decrypted by the other – for example, on a laptop. No one, including your Internet service provider will not be able to decrypt your message. Compare this encryption type with another type when you establish the connection via your ISP, for example, via HTTPS connection. HTTPS will protect your message from potential snoopers on Wi-Fi like teenagers with Wireshark installed or your service provider, but will not be able to protect the message from the company on the other end of your connection – for example, Google or Facebook – as well as from law enforcement and intelligence services, requesting information from those companies.
Another, no less important is the need to protect not only the contents of your communication, and its metadata. Some metadata, such as who is talking to whom, can play a very important role. If someone is going to contact the journalist, one of encryption of a letter will not be enough to hide the fact of correspondence with the journalist. Similarly, if you are star-crossed lovers trying to connect with each other and keep it a secret from their warring families, you will have to hide not only the content of your love letters, but the fact that you basically go to the link. Let's briefly examine how it can be done.
Concealment linetypescale that Juliet is trying to get in touch with Romeo. They both know that if they use phone, email, Skype, or other traditional methods, they can't hide from their powerful families and the fact that they are in contact. The trick is to hide rather not what they communicated and what they are – Romeo and Juliet.
Juliet and Romeo decided to have a new account for communication. Juliet took the pseudonym "Ceres", and Romeo took the name "Eris". Now that Ceres and Eris can exchange encrypted messages, to find out what these names are Juliet and Romeo, will be much harder. If the account Juliet will check for the existence of a relationship with Romeo and her irascible cousin, to put it mildly, a bit arrogant, then no evidence will not be found.
Of course, it is not enough just to rename myself. At this stage it is still possible, and sometimes even quite simply, to find out what Ceres is hiding under Juliet, and under the Erys – Romeo.
Juliet comes in to your account under the name "Ceres" from the same IP address that it uses for other purposes on your computer (for example, when associated with his brother Lorenzo via e-mail). If her activity on the Internet is tracked (and it is, for sure, because all of our activity online is tracked), to compare the number of facts will be easy. If the service is forced to hand over IP address from which the user "Ceres" is coming on line, it can easily be mapped with an IP address of Juliet. The same problem arises and at Romeo.
From independent services, such as telecommunications companies and email domains have access to private information about their users, and, according to the "doctrine of the third person" the users "can't expect hiding" such information. This principle applies not only to the secret lovers: journalists can obtain a number of privileges in accordance with the First amendment of the US Constitution, should closely monitor those who are responsible for the services their communication. In 2013, the U.S. Department of Justice received information about a number of phone calls made by Associated Press journalists, in the course of the investigation about the leak of information. Many news outlets not immutableimage mail service: the New York Times and Wall Street Journal use Google mail, USA Today uses the services of Microsoft – so the US Government can request data. (Published by The Intercept uses its own email service).
Anonymityin order to conceal his private correspondence, Juliette must make a clear distinction between the account of Ceres and his real personality. By far the most simple and safe method is to use a decentralized anonymous network, open source under the name Tor.
Tor is for anonymous use of the Internet. It is a decentralized network of random "nodes" – computers, which transmit and execute the queries on the Internet on behalf of other computers. Tor allows you to stay anonymous by connecting you to the Internet through a series of such nodes. If at least one of the nodes was placed in a series of intentional, no one will be able to know who you are and what you do: you either know your IP address without knowing what you are doing on the Network, or to find out what you do online, and not know your IP address.
Most of those who heard about the Tor network, and know about the eponymous browser that you can use for anonymous browsing web pages. But in addition, its software can be used anonymously and for other purposes, including messaging and emails.
If Romeo and Juliet use the Tor network to access their accounts, Eris and Ceres, and if they will exchange messages with the encryption Protocol OTR, they will finally be able to organize your personal online correspondence regardless of whether to follow them or not.
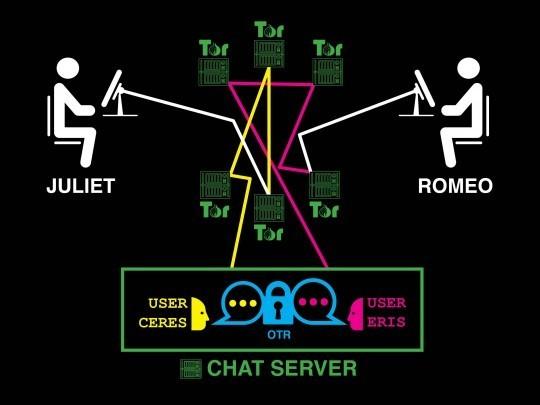
Romeo and Juliet secretly to exchange encrypted messages with an anonymous account
Hackers are all around us from all storeapart when Romeo and Juliet have created a new anonymous account in the Tor network, let's test all the parts of our system in the presence of faults.
From Juliet: an attacker that monitors Internet traffic Juliet, will be able to see that her traffic partially goes through Tor, but can't understand why Juliet uses it. If hackers will start to check to whom Juliet writes e-mails, with whom she communicates via Skype who calls and who sends the messages, the signs of her relationship with Romeo is found. (Of course, the use of the Tor network itself can arouse suspicion. Therefore, The Intercept for anonymity encourages from your PC network connection, not connected with the organization of the service provider. In other words, to protect yourself, Juliet could access the Internet from Starbucks or the public library).
From Romeo: an attacker monitoring the Internet traffic of Romeo, will be able to see that traffic partially goes through Tor. If this person will scan all mail, calls, messages, and activity in Skype Romeo, then Juliet it is not.
From the instant messaging server: the messaging service itself can keep track of what someone with an IP address in the Tor network have created a user "Ceres", someone with an IP address in the Tor network have created a user "Eris", and both of you exchange with each other encrypted messages. You don't know what Ceres is actually Juliet, or that Eris is in fact Romeo, as their IP addresses hides Tor. It is also impossible to know what Ceres and Eris speak to each other because their messages are encrypted using OTR. These accounts could just as easily belong to the informant and the journalist or human rights activist and lawyer, not two lovers, who exchange verses.
Even after the adoption of these measures remains a small proportion of metadata that can leak, if you act carelessly. Here's what you need to remember:
Tor has never been a reliable defense against "global observer" – forces that can monitor all network nodes in real time around the world. These forces could monitor the traffic of Tor users are within the network, monitor the movement of traffic around the world and then watch as this traffic leaves the network, thereby explaining what traffic belongs to a particular user.
But despite all this, the Snowden documents published by The Guardian, indicate that the joint spy force "Five eyes" [eng. Five Eyes] (USA, UK, Canada, Australia and New Zealand) are not yet considered to be "global observer": at least, they were not considered as such in July 2012, when there was held the presentation of these top-secret materials. As it turned out, Western intelligence agencies can only expose a random unlucky user for their own benefit and have never been able to expose a specific user on demand.
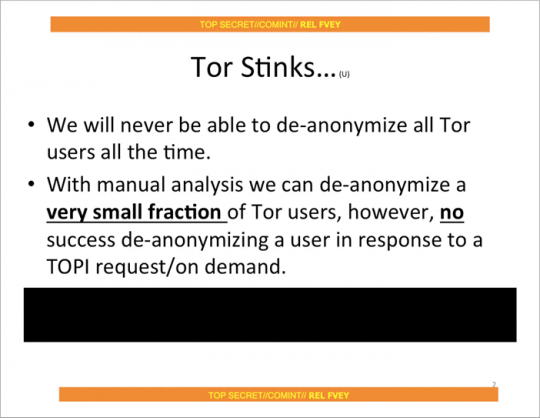
As promising as it sounds, Tor is not always able to conceal your identity, especially if you are already under surveillance. A striking example is the arrest of Jeremy Hammond.
The FBI suspected that Hammond may be a member of hacker group LulzSec, who continued to commit cyber crimes in 2011. In particular, the FBI believed that it can work in the online chat under the pseudonym sup_g. His staff set up surveillance in the apartment Hammond in Chicago, watching what servers he was connected on my Wi-Fi network. In a sworn document, the FBI States that "a significant portion of traffic came from Chicago apartments [Hammond] the Internet via the Tor network". The FBI conducted a low-tech correlation attack traffic to confirm that Hammond was in fact operated under the name sup_g. When Hammond left his apartment, the traffic on the Tor network ceased, and sup_g left the chat. When he came home, the traffic was resumed, and sup_g again appeared in the network. Because he was the Prime suspect, Tor could no longer conceal his identity.
Tor is not something supernatural; it is only a tool. The person who uses it, be aware of the activities of the FBI, if he wishes to remain anonymous.
Workstation security, you Can make another reservation. If a hacker hacks into the computer of Juliet, he will be able to know what she was doing. The same situation with Romeo. You can encrypt all traffic and use all nodes of the world to protect your data, but if a hacker can see the text you type, and your computer screen, you will never be away from him.
It is extremely difficult to protect your computer from attacks, if you are hunting hackers with great potential. You can reduce the risk of hacking your computer, if you use a separate device exclusively for a protected connection, because the computer that you use for everyday tasks, will crack much easier.
In addition, personal correspondence you can use a tool such as Tails. It is a portable operating system that can be installed on a flash drive and anonymously to work with it, even if hackers hacked your normal operating system. Despite the fact that Tails will provide you with a high degree of protection in the conduct of personal correspondence, it is a rather complex tool. New users will have to spend several days to resolve different kinds of problems, especially if they are not familiar with Linux.
Most of the users are satisfied with their conventional operating system with which you can exchange private messages in real time and not worry about what you can crack – although in this case, the possibility of leakage of data that you would like to keep secret, is higher. This option is much more convenient and easier to start work if you only need a little personal space, and you have no important data that can be compromised.
First contactWhen you going to start an online correspondence, is not always clear exactly how to do it. If you can meet the person personally, then establish a secure communication channel is quite simple: at the meeting we just need to know each other's logins, the im server messaging and OTR fingerprints (for details see below).
However, it is not always possible to meet in person: you can be located at a great distance from each other or one party may want to remain unknown for another. Even if you both want to meet in person, as you agree, if you need to hide the fact that you keep in touch with each other?
In order to establish a first contact with Romeo, Juliet should be specially for this is to create an anonymous account, which will allow her to communicate with the public account of Romeo. It may poison Romeo an email from your anonymous email. Most email services when creating an account requires the user's phone number and some closed access to all users of the Tor network, therefore creating an anonymous account is complicated. Juliet could also create an anonymous account on the social network and use it to communicate with the public profile of Romeo.
If possible they should first encrypt the messages she sends to Romeo. The procedure is simplified if Romeo will publish a PGP key. All The Intercept journalists publish their PGP keys on a page of staff profiles. If you are going to make first contact with a journalist working in an organization that uses the platform SecureDrop, you can use it to create a new anonymous account and not have to deal with PGP keys. SecureDrop is used in The Intercept.
At the first contact with Romeo Juliet must specify a chat server on which you created an account, your username, OTR fingerprint and time when she would wait in the network. In addition, it can give Romeo the necessary instructions to create an account, perhaps referring to this article.
If Juliet and Romeo walked to their anonymous accounts and started to exchange encrypted messages with OTR fingerprints, the case is almost done. Depending on how Juliet made first contact with Romeo, a careful study of the letters of Romeo and his account on the social network may disclose the user data of the anonymous account Juliet: anyway, she must tell him the data. So investigators can find out and hidden profile Romeo.
To prevent such a situation, Juliet and Romeo can delete their accounts and go to new, leaving no traces. In fact, Juliet and Romeo must leave their old account when they see fit, and go to new accounts with new keys OTR encryption. There are hundreds of public chat servers and create a new account is completely free.
From theory to practiceNow that you are familiar with the theory of concealing their identity, the time has come for its practical application.
Don't worry, I'm sure you will succeed. You will only need to follow the instructions suggested for users of Mac OS X, Windows, Linux and Android. (Sorry, anonymous contact through the chat server on the iPhone will not work). For starters, practice with a friend.
Jabber and Off-the-RecordWhen I talked about "chat server", I actually meant the Jabber server, also known as XMPP. Jabber is an open Protocol for instant messaging; it's not a special service Signal such as, WhatsApp or Facebook. Jabber is a decentralized integrated application like email. I can send email from your mailbox @theintercept.com on your gmail.com because the servers The Intercept's and Gmail work on a single, standard Protocol.
So everyone has the opportunity to run a Jabber server: it is a variety of organizations, including the Calyx Institute, Riseup, the Chaos Computer Club and DuckDuckGo and others. There are hundreds of other public Jabber servers. Many organizations work on private servers, Jabber, including a subsidiary of The Intercept called First Look Media. The messaging service HipChat runs on Jabber, and his competitor, Slack, uses the Jabber gateways.
Since Jabber is decentralized, a user with Jabber account like akiko@jabber.calyxinstitute.org may correspond with boris@dukgo.co. But if both parties – Romeo and Juliet in this example – use the same server for their accounts in Jabber, the metadata of their correspondence will be better protected. Messages will be stored on a single server and are never transmitted over the Internet.
Unlike email, most Jabber servers allow users to create accounts via Tor and do not require from you any personal information. Generally speaking, many Jabber servers run anonymous services that allow Tor users to communicate with each other, without departing from the network. This topic is quite complicated, so for simplicity I will not use anonymous services in the description of instructions in the future.
Off-the-Record (OTR) is a encryption Protocol, which can add encryption between end users in any messaging service, including Jabber. To exchange encrypted messages, both parties must use software that supports encryption Protocol OTR. There are several options, but this article describes the application Adium for Mac users, Pidgin for Windows and Linux and ChatSecure for Android users. ChatSecure is also available in iOS, but the app is not up to the end compatible with Tor on iOS devices.
Choose a Jabber serverIf you are going to conceal his identity by creating an account on the Android platform, you can go to the appropriate section. In ChatSecure for Android has built-in support to create temporary anonymous accounts to conceal identity.
All the rest you need to download and install Tor browser. Open it and download a copy of our article in the browser, not the one that you used previously. So now you use the Tor browser. This is very important, because I don't want your IP address got lost in the log files of each server Jabber that you intend to use it. As will be shown later, this will be the main idea of disclosing your identity.
You have a choice of hundreds of Jabber servers. We can find a list of public Jabber servers. Which one should I choose?
The server will not be able to determine who you really are (you connect via Tor) or what you write in your posts (you will use the OTR Protocol to encrypt their messages), so you don't need to worry about it. However, it is better to choose a server that is less likely to transmit the log files from your government, and it would not be very happy that the users of the Tor network to create anonymous accounts.
Most people are creating accounts in Jabber directly with programs to exchange messages. To configure a program to send messages through Tor while in their account, it's easy. Harder to ensure that the program allows you to create through Tor new accounts (if you work in operating system Tails, then you have nothing to worry about, as all your traffic will pass through the Tor network). In this regard, I recommend to choose a Jabber server that will allow you to create a new account from the website, you can do this in Tor browser is a program for messaging.
Here are a few Jabber servers where you can create a new account using the Tor browser. They are selected randomly from the list of public servers: ChatMe (located in Italy), CodeRollers (located in Romania), Darkness XMPP (located in Russia), KodeRoot (located in USA), Jabber.at (located in Austria), Hot-Chilli (located in Germany), XMPP.jp (located in Japan), etc. the List is pretty big.
Ready to get started? Select the Jabber server. Create a username unrelated to your real identity. Create a password that you never use.
Create an account in Jabber using the Tor browser. Now write the data of the server on which you created an account your username and password and proceed to the next section depending on the platform you use: Android, Mac OS X, Windows or Linux.
Select your operating system:
(Yet there is no guide for iOS, as, despite the fact that ChatSecure for iOS has experimental support Tor developers don't recommend you to count on complete anonymity, while experts in the field of security will not conduct a thorough check of the application).
Anonymous transmission of encrypted messages in Mac OS XIf you have not yet created a new account in Jabber using the Tor browser, create it in accordance with the instructions in the section "Choose Jabber server", located above. Make sure you know which server you created your account and your username and password.
For this example I created a account in Jabber server xmpp.jp and get the login pluto1.
Install Adium and configure the anonymous account via Tor,Download and install the Adium client for messaging for Mac, which supports the encryption Protocol OTR.
Make sure the Tor browser is open. While it is open, Tor is running on your computer in the background. When you close the Tor browser, a service Top will also stop their work. This means that every time you want to use your hidden account in Jabber, your Tor browser should be run in the background, otherwise Adium just can't connect. So, open the Tor browser and do not close it until you have completed all instructions.
Open Adium. Once you open this, you will see the window Adium Assistant Wizard. Close: we will create the account manually to get the additional features.
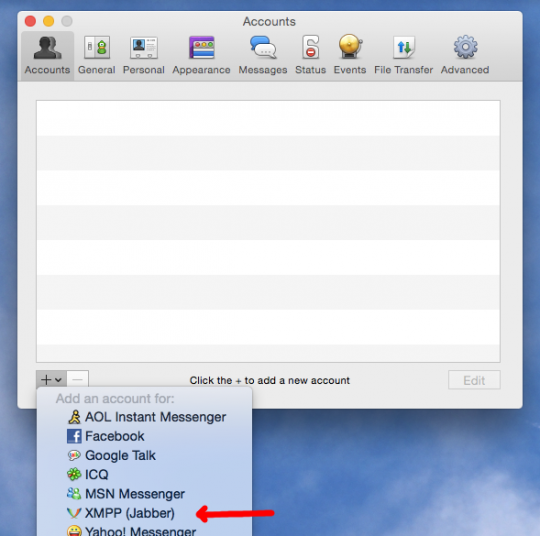
Selecting the window "Contacts" (Contacts), click on the menu bar at the top of Adium and select "Settings" (Preferences). Make sure that the selected tab is "Account" (Accounts) to the top of the window. Click on the "+" button in the bottom left of the window to add a new account. Then in the drop-down list, select "XMPP (Jabber)".
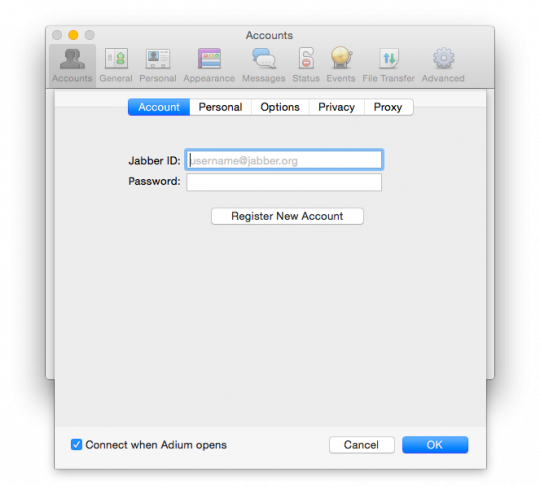
After that will appear a new dialog box where you can set the settings for your account.
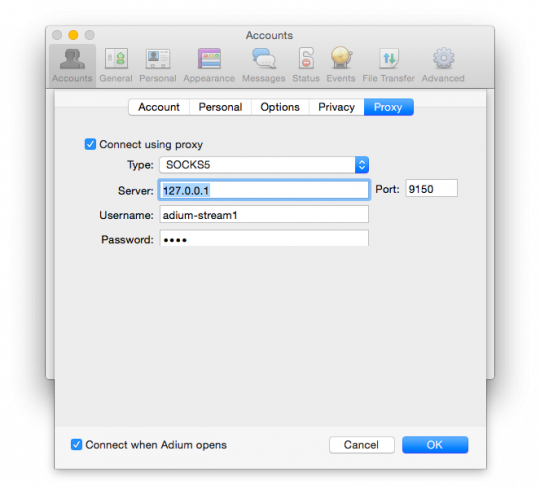
Before proceeding to the next step, switch to the tab "Proxy" (Connect using proxy) and select type "SOCKS5". In the "Server" field, enter "127.0.0.1" and the Port box type "9150". Think of this account with a user name and password and enter them in corresponding fields. These settings ensure that Adium will connect to that account through Tor. To enter a user name and password are not required, but if you are going to use them, then Tor will pick up for this account, distinct from other communication channels, which will increase your anonymity.
Go to the tab "Security" (Privacy). In the "Encryption" (Encryption) change the value from "Encrypt messages on request" (Encrypt chats as requested) to "Conduct mandatory encryption to prevent plaintext" (Force encryption and refuse plaintext).
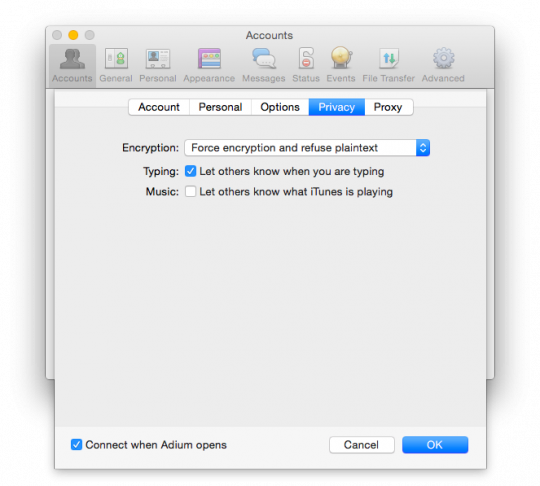
Go to the tab "Settings" (Options). Change the field "Resource" (Resource) (the default name of your computer) to "anonymous". In addition, the item "Security" (Security) check the box next to "Require SSL/TLS" (Require SSL/TLS).
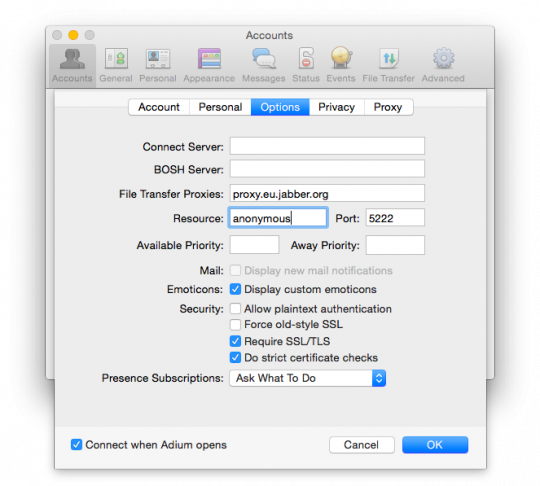
Now go to the tab "Account" (Account). Enter the Jabber ID. Username – pluto1, the server name of the Jabber xmpp.jp, therefore, the Jabber ID will be recorded as pluto1@xmpp.jp. Enter your password and click "OK" to log in to your account.
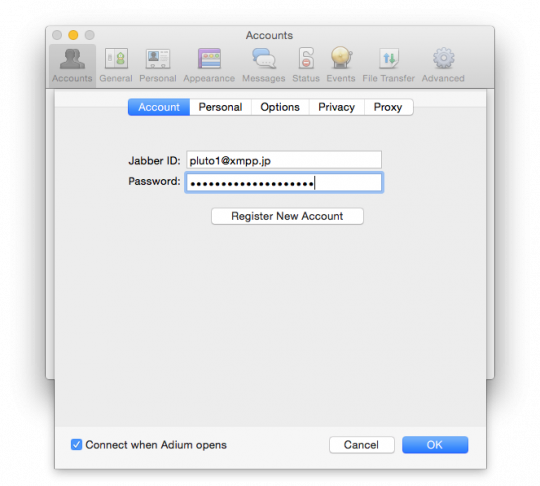
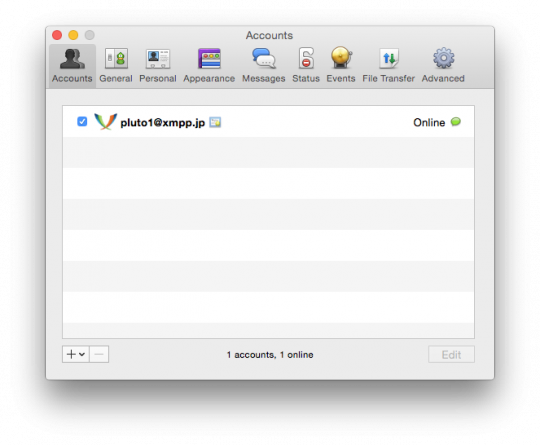
Now Adium will attempt to connect to your anonymous account through Tor. If all goes well, in the list of accounts should appear in your account with the caption "Online".
Encryption keys and printsso you anonymously included in their hidden account via Tor. Next step is to create the encryption key according to the OTR Protocol. Everyone who wants to use the OTR Protocol must generate a private key. This key is a file stored on the device you use for messaging. Each key contains a unique sequence of characters called a fingerprint of this key: no two keys can have the same fingerprint.
Try to create your key with encryption via the OTR. In the window "Contacts" (Contacts), click on the Adium menu bar and select "Preferences" (Preferences). Go to the "Advanced" tab (Advanced) and click on the sidebar "Encryption" (Encryption). Select the anonymous account and click "Generate" (Generate) button to generate a new key. After the procedure is completed you will have new fingerprint encrypted by OTR.
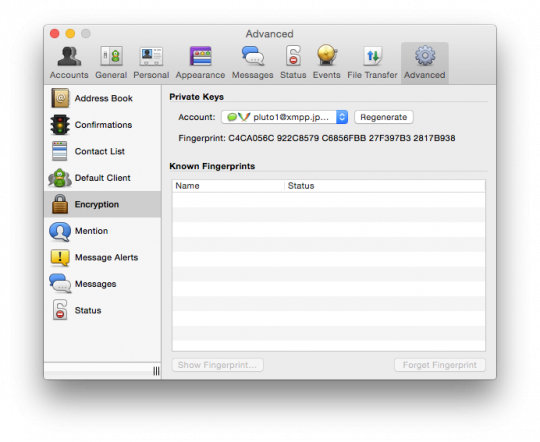
In our example, I created a new key, using the encryption OTR for your account pluto1@xmpp.jp with the imprint C4CA056C 922C8579 C6856FBB 27F397B3 2817B938. If you want to start with someone personal correspondence, inform that person your login and server name and key fingerprint OTR. After it will create an anonymous account in Jabber and generate a key encrypted with OTR, and ask them to tell you your username, server name and key fingerprint.
After the exchange of encrypted messages, you will be able to see the key fingerprint of his companion, and he will be able to see your. If the print delivered to you, coincides with the imprint that appears in Adium, the contact can be marked as reliable. If the print that gave you matches the fingerprint that is displayed in Adium, then your contact may also be marked as reliable.
This step is somewhat involved, but very important. If the key fingerprint does not match, it means that you are targeted by the attack of a mediator. In this case, do not mark the contact as a reliable, and try to repeat the procedure later.
Adding contacts and personal correspondenceI'm trying to start private messaging with a friend. He told me that his account in Jabber pluto2@wtfismyip.com and OTR-fingerprint – A65B59E4 0D1FD90D D4B1BE9F F9163914 46A35AEE.
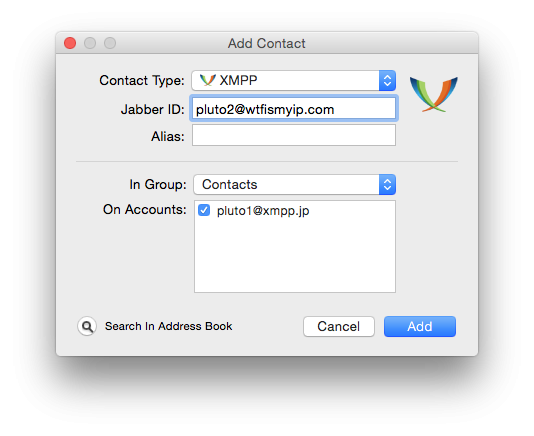
After I created my account pluto1, I want to add user pluto2 to his contacts. First, I choose the window "Contacts" (Contacts) and then click on the menu "Contact" and select "Add contact" (Add Contact). In the "Type of contact" (Contact Type) I choose XMPP, and the Jabber ID enter "pluto2@wtfismyip.com". Then click on the "Add" button (Add) to add a user to your contact list.
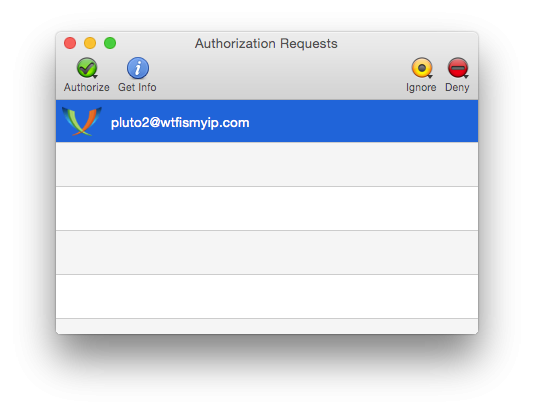
After you have added a contact in Jabber, you can't immediately determine it is in network or not. First you need to obtain consent to view its status. So now I have to wait until pluto2 enters in to your account and confirm my request to add to contacts.
So pluto2 allowed me to see when he is online, he sends a request to me to let him see when I am online. I choose the contact and click on the "Allow to add me to your list of contacts" (Authorize).
Now I first added user pluto2 as your contact and it will appear in my contact list, when will be online. Then all I need to do to begin with is to double-click on its name.
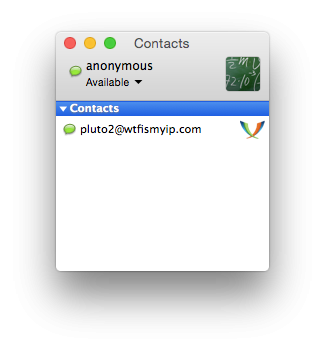
I clicked twice on the contact pluto2 wrote, "hi."
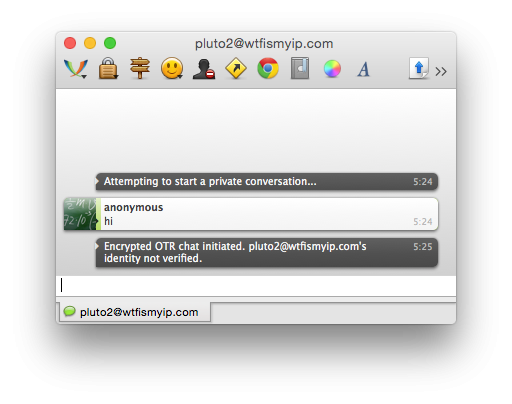
Before to send my message, Adium started the session with OTR encryption. Note the inscription "personality pluto2@wtfismyip.com not confirmed" (pluto2@wtfismyip.com's identity not verified). This means that during the exchange of encrypted messages I can't be sure that will not happen the attacks of the mediator.
In addition, POPs up a dialog box "Confirm imprint OTR" (OTR Fingerprint Verification box). Does the imprint which gave me the user pluto2, with what is written in this window?
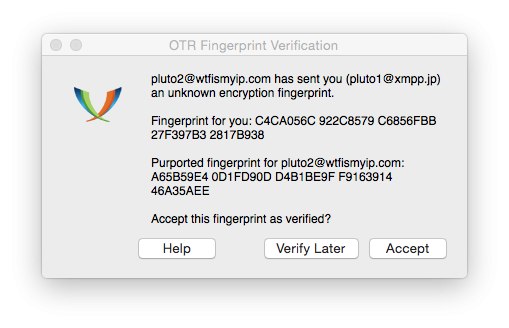
I compare each of the symbols imprint, which pluto2 gave me earlier, with the characters of the thumbprint referenced in Adium. It is seen that they are really the same. So, no one proceeds to attack the encryption, I can press the button "Accept" (Accept). If I didn't have an OTR fingerprint pluto2, I would have asked for it pluto2 external [eng. out-of-band] channel (not in this chat, as I don't know how reliable it is), and then confirmed that they match. If I didn't have time for this, I would have clicked on the button "Confirm later" (Verify Later).
You need to go step confirmation just before the exchange of encrypted messages with the new contact. If tomorrow I go to my account and start a conversation with pluto2, I can immediately start working, considering this conversation is protected.
That's all. The result: we created an anonymous account in Jabber through the Tor network. We set up a program to exchange messages and Adium can log into this account via Tor. We have created a new OTR key encryption for this account. We have added in to your account one contact and checked the print OTR encryption. Now we can share with the contact reports at a high enough level of information protection.published
To be continued...
P. S. And remember, only by changing their consumption — together we change the world! © Join us at Facebook , Vkontakte, Odnoklassniki
Source: habrahabr.ru/company/it-grad/blog/271165/
When you pick up the phone and make a call, send SMS, email, post to Facebook or Google Hangouts, others can track what you say, who're talking and where you are. This personal information may be available not only to the service provider who acts as a mediator in your conversation, but telecommunications companies, which provides access to the Internet, the intelligence services and law enforcement agencies, and even a few teenagers that can track your actions in a Wi-Fi network using the application Wireshark.
However, if you take the necessary steps to protect your information, you will be able to send secret and anonymous online messages. In this article I will in detail tell about how to do it. We will consider the methods by which two and a half years ago, I used the informant and ex-NSA employee Edward Snowden to contact me. In other words, I will show you how to create an anonymous account for online correspondence and exchange of messages using encryption Protocol called Off-the-Record Messaging, or OTR.
If you don't want to read the entire article, you can skip to the section where the phases described how to create account on Mac OS X, Windows, Linux and Android. When you have enough time, go back to the beginning and read the important points that go to these sections.

First, you need to make sure that you are using encryption between the end-users [eng. end-to-end encryption]. In this case, the message is encrypted on one end – say, on a smartphone – and decrypted by the other – for example, on a laptop. No one, including your Internet service provider will not be able to decrypt your message. Compare this encryption type with another type when you establish the connection via your ISP, for example, via HTTPS connection. HTTPS will protect your message from potential snoopers on Wi-Fi like teenagers with Wireshark installed or your service provider, but will not be able to protect the message from the company on the other end of your connection – for example, Google or Facebook – as well as from law enforcement and intelligence services, requesting information from those companies.
Another, no less important is the need to protect not only the contents of your communication, and its metadata. Some metadata, such as who is talking to whom, can play a very important role. If someone is going to contact the journalist, one of encryption of a letter will not be enough to hide the fact of correspondence with the journalist. Similarly, if you are star-crossed lovers trying to connect with each other and keep it a secret from their warring families, you will have to hide not only the content of your love letters, but the fact that you basically go to the link. Let's briefly examine how it can be done.
Concealment linetypescale that Juliet is trying to get in touch with Romeo. They both know that if they use phone, email, Skype, or other traditional methods, they can't hide from their powerful families and the fact that they are in contact. The trick is to hide rather not what they communicated and what they are – Romeo and Juliet.
Juliet and Romeo decided to have a new account for communication. Juliet took the pseudonym "Ceres", and Romeo took the name "Eris". Now that Ceres and Eris can exchange encrypted messages, to find out what these names are Juliet and Romeo, will be much harder. If the account Juliet will check for the existence of a relationship with Romeo and her irascible cousin, to put it mildly, a bit arrogant, then no evidence will not be found.
Of course, it is not enough just to rename myself. At this stage it is still possible, and sometimes even quite simply, to find out what Ceres is hiding under Juliet, and under the Erys – Romeo.
Juliet comes in to your account under the name "Ceres" from the same IP address that it uses for other purposes on your computer (for example, when associated with his brother Lorenzo via e-mail). If her activity on the Internet is tracked (and it is, for sure, because all of our activity online is tracked), to compare the number of facts will be easy. If the service is forced to hand over IP address from which the user "Ceres" is coming on line, it can easily be mapped with an IP address of Juliet. The same problem arises and at Romeo.
From independent services, such as telecommunications companies and email domains have access to private information about their users, and, according to the "doctrine of the third person" the users "can't expect hiding" such information. This principle applies not only to the secret lovers: journalists can obtain a number of privileges in accordance with the First amendment of the US Constitution, should closely monitor those who are responsible for the services their communication. In 2013, the U.S. Department of Justice received information about a number of phone calls made by Associated Press journalists, in the course of the investigation about the leak of information. Many news outlets not immutableimage mail service: the New York Times and Wall Street Journal use Google mail, USA Today uses the services of Microsoft – so the US Government can request data. (Published by The Intercept uses its own email service).
Anonymityin order to conceal his private correspondence, Juliette must make a clear distinction between the account of Ceres and his real personality. By far the most simple and safe method is to use a decentralized anonymous network, open source under the name Tor.
Tor is for anonymous use of the Internet. It is a decentralized network of random "nodes" – computers, which transmit and execute the queries on the Internet on behalf of other computers. Tor allows you to stay anonymous by connecting you to the Internet through a series of such nodes. If at least one of the nodes was placed in a series of intentional, no one will be able to know who you are and what you do: you either know your IP address without knowing what you are doing on the Network, or to find out what you do online, and not know your IP address.
Most of those who heard about the Tor network, and know about the eponymous browser that you can use for anonymous browsing web pages. But in addition, its software can be used anonymously and for other purposes, including messaging and emails.
If Romeo and Juliet use the Tor network to access their accounts, Eris and Ceres, and if they will exchange messages with the encryption Protocol OTR, they will finally be able to organize your personal online correspondence regardless of whether to follow them or not.

Romeo and Juliet secretly to exchange encrypted messages with an anonymous account
Hackers are all around us from all storeapart when Romeo and Juliet have created a new anonymous account in the Tor network, let's test all the parts of our system in the presence of faults.
From Juliet: an attacker that monitors Internet traffic Juliet, will be able to see that her traffic partially goes through Tor, but can't understand why Juliet uses it. If hackers will start to check to whom Juliet writes e-mails, with whom she communicates via Skype who calls and who sends the messages, the signs of her relationship with Romeo is found. (Of course, the use of the Tor network itself can arouse suspicion. Therefore, The Intercept for anonymity encourages from your PC network connection, not connected with the organization of the service provider. In other words, to protect yourself, Juliet could access the Internet from Starbucks or the public library).
From Romeo: an attacker monitoring the Internet traffic of Romeo, will be able to see that traffic partially goes through Tor. If this person will scan all mail, calls, messages, and activity in Skype Romeo, then Juliet it is not.
From the instant messaging server: the messaging service itself can keep track of what someone with an IP address in the Tor network have created a user "Ceres", someone with an IP address in the Tor network have created a user "Eris", and both of you exchange with each other encrypted messages. You don't know what Ceres is actually Juliet, or that Eris is in fact Romeo, as their IP addresses hides Tor. It is also impossible to know what Ceres and Eris speak to each other because their messages are encrypted using OTR. These accounts could just as easily belong to the informant and the journalist or human rights activist and lawyer, not two lovers, who exchange verses.
Even after the adoption of these measures remains a small proportion of metadata that can leak, if you act carelessly. Here's what you need to remember:
- Be sure to use Tor when creating an account to exchange messages, not only when you are in conversation.
- Never go to your account, if you are not in the Tor network.
- Make sure that your username do not reveal your true identity: for example, do not use the login that you have once enjoyed. Instead, you can take a random name that has nothing to do with you. Often, many believe that the anonymous account should be your "second self". These people come up with a cool username, and then become attached to it. However, it is better to treat its new name, as something disposable or temporary: your task is to hide the hidden identity, and not to put it on public display. A set of random characters like "bk7c7erd19" fits as a name much better than "gameofthronesfan".
- Do not use a password you already use elsewhere. Reuse of passwords not only will reduce your level of safety, but also to expose you if the account that is somehow tied to your real identity, enter the same password as in your anonymous account.
- Be careful with whom you contact and through which one of the anonymous accounts. If one of your contacts is not protected, it can increase the chances that other contacts will also be unprotected. It would be logical to create a separate account for each project or contact, to reduce the risk of exposing the whole network of anonymous contacts.
- Do not enter any personal data in the messaging service.
- Keep track of your habits. If you log in to your account in the morning when start to use the computer and get out of it in the evening after work, the service will store information about in what time zone you are in and what time you work. For you it may be not so important, but if important, it is better to negotiate with the partner about a time when you will be online.
- Be careful how you use your IP address to Tor. If you use Tor for anonymous account and a regular account which has to you something, the record in the server log can indicate the relationship between your anonymous account and your real personality. With a unique login and password for the SOCKS Protocol you can configure Tor so that in each of your accounts will work in different communication channels. In the future, this will be discussed in more detail.
Tor has never been a reliable defense against "global observer" – forces that can monitor all network nodes in real time around the world. These forces could monitor the traffic of Tor users are within the network, monitor the movement of traffic around the world and then watch as this traffic leaves the network, thereby explaining what traffic belongs to a particular user.
But despite all this, the Snowden documents published by The Guardian, indicate that the joint spy force "Five eyes" [eng. Five Eyes] (USA, UK, Canada, Australia and New Zealand) are not yet considered to be "global observer": at least, they were not considered as such in July 2012, when there was held the presentation of these top-secret materials. As it turned out, Western intelligence agencies can only expose a random unlucky user for their own benefit and have never been able to expose a specific user on demand.

As promising as it sounds, Tor is not always able to conceal your identity, especially if you are already under surveillance. A striking example is the arrest of Jeremy Hammond.
The FBI suspected that Hammond may be a member of hacker group LulzSec, who continued to commit cyber crimes in 2011. In particular, the FBI believed that it can work in the online chat under the pseudonym sup_g. His staff set up surveillance in the apartment Hammond in Chicago, watching what servers he was connected on my Wi-Fi network. In a sworn document, the FBI States that "a significant portion of traffic came from Chicago apartments [Hammond] the Internet via the Tor network". The FBI conducted a low-tech correlation attack traffic to confirm that Hammond was in fact operated under the name sup_g. When Hammond left his apartment, the traffic on the Tor network ceased, and sup_g left the chat. When he came home, the traffic was resumed, and sup_g again appeared in the network. Because he was the Prime suspect, Tor could no longer conceal his identity.
Tor is not something supernatural; it is only a tool. The person who uses it, be aware of the activities of the FBI, if he wishes to remain anonymous.
Workstation security, you Can make another reservation. If a hacker hacks into the computer of Juliet, he will be able to know what she was doing. The same situation with Romeo. You can encrypt all traffic and use all nodes of the world to protect your data, but if a hacker can see the text you type, and your computer screen, you will never be away from him.
It is extremely difficult to protect your computer from attacks, if you are hunting hackers with great potential. You can reduce the risk of hacking your computer, if you use a separate device exclusively for a protected connection, because the computer that you use for everyday tasks, will crack much easier.
In addition, personal correspondence you can use a tool such as Tails. It is a portable operating system that can be installed on a flash drive and anonymously to work with it, even if hackers hacked your normal operating system. Despite the fact that Tails will provide you with a high degree of protection in the conduct of personal correspondence, it is a rather complex tool. New users will have to spend several days to resolve different kinds of problems, especially if they are not familiar with Linux.
Most of the users are satisfied with their conventional operating system with which you can exchange private messages in real time and not worry about what you can crack – although in this case, the possibility of leakage of data that you would like to keep secret, is higher. This option is much more convenient and easier to start work if you only need a little personal space, and you have no important data that can be compromised.
First contactWhen you going to start an online correspondence, is not always clear exactly how to do it. If you can meet the person personally, then establish a secure communication channel is quite simple: at the meeting we just need to know each other's logins, the im server messaging and OTR fingerprints (for details see below).
However, it is not always possible to meet in person: you can be located at a great distance from each other or one party may want to remain unknown for another. Even if you both want to meet in person, as you agree, if you need to hide the fact that you keep in touch with each other?
In order to establish a first contact with Romeo, Juliet should be specially for this is to create an anonymous account, which will allow her to communicate with the public account of Romeo. It may poison Romeo an email from your anonymous email. Most email services when creating an account requires the user's phone number and some closed access to all users of the Tor network, therefore creating an anonymous account is complicated. Juliet could also create an anonymous account on the social network and use it to communicate with the public profile of Romeo.
If possible they should first encrypt the messages she sends to Romeo. The procedure is simplified if Romeo will publish a PGP key. All The Intercept journalists publish their PGP keys on a page of staff profiles. If you are going to make first contact with a journalist working in an organization that uses the platform SecureDrop, you can use it to create a new anonymous account and not have to deal with PGP keys. SecureDrop is used in The Intercept.
At the first contact with Romeo Juliet must specify a chat server on which you created an account, your username, OTR fingerprint and time when she would wait in the network. In addition, it can give Romeo the necessary instructions to create an account, perhaps referring to this article.
If Juliet and Romeo walked to their anonymous accounts and started to exchange encrypted messages with OTR fingerprints, the case is almost done. Depending on how Juliet made first contact with Romeo, a careful study of the letters of Romeo and his account on the social network may disclose the user data of the anonymous account Juliet: anyway, she must tell him the data. So investigators can find out and hidden profile Romeo.
To prevent such a situation, Juliet and Romeo can delete their accounts and go to new, leaving no traces. In fact, Juliet and Romeo must leave their old account when they see fit, and go to new accounts with new keys OTR encryption. There are hundreds of public chat servers and create a new account is completely free.
From theory to practiceNow that you are familiar with the theory of concealing their identity, the time has come for its practical application.
Don't worry, I'm sure you will succeed. You will only need to follow the instructions suggested for users of Mac OS X, Windows, Linux and Android. (Sorry, anonymous contact through the chat server on the iPhone will not work). For starters, practice with a friend.
Jabber and Off-the-RecordWhen I talked about "chat server", I actually meant the Jabber server, also known as XMPP. Jabber is an open Protocol for instant messaging; it's not a special service Signal such as, WhatsApp or Facebook. Jabber is a decentralized integrated application like email. I can send email from your mailbox @theintercept.com on your gmail.com because the servers The Intercept's and Gmail work on a single, standard Protocol.
So everyone has the opportunity to run a Jabber server: it is a variety of organizations, including the Calyx Institute, Riseup, the Chaos Computer Club and DuckDuckGo and others. There are hundreds of other public Jabber servers. Many organizations work on private servers, Jabber, including a subsidiary of The Intercept called First Look Media. The messaging service HipChat runs on Jabber, and his competitor, Slack, uses the Jabber gateways.
Since Jabber is decentralized, a user with Jabber account like akiko@jabber.calyxinstitute.org may correspond with boris@dukgo.co. But if both parties – Romeo and Juliet in this example – use the same server for their accounts in Jabber, the metadata of their correspondence will be better protected. Messages will be stored on a single server and are never transmitted over the Internet.
Unlike email, most Jabber servers allow users to create accounts via Tor and do not require from you any personal information. Generally speaking, many Jabber servers run anonymous services that allow Tor users to communicate with each other, without departing from the network. This topic is quite complicated, so for simplicity I will not use anonymous services in the description of instructions in the future.
Off-the-Record (OTR) is a encryption Protocol, which can add encryption between end users in any messaging service, including Jabber. To exchange encrypted messages, both parties must use software that supports encryption Protocol OTR. There are several options, but this article describes the application Adium for Mac users, Pidgin for Windows and Linux and ChatSecure for Android users. ChatSecure is also available in iOS, but the app is not up to the end compatible with Tor on iOS devices.
Choose a Jabber serverIf you are going to conceal his identity by creating an account on the Android platform, you can go to the appropriate section. In ChatSecure for Android has built-in support to create temporary anonymous accounts to conceal identity.
All the rest you need to download and install Tor browser. Open it and download a copy of our article in the browser, not the one that you used previously. So now you use the Tor browser. This is very important, because I don't want your IP address got lost in the log files of each server Jabber that you intend to use it. As will be shown later, this will be the main idea of disclosing your identity.
You have a choice of hundreds of Jabber servers. We can find a list of public Jabber servers. Which one should I choose?
The server will not be able to determine who you really are (you connect via Tor) or what you write in your posts (you will use the OTR Protocol to encrypt their messages), so you don't need to worry about it. However, it is better to choose a server that is less likely to transmit the log files from your government, and it would not be very happy that the users of the Tor network to create anonymous accounts.
Most people are creating accounts in Jabber directly with programs to exchange messages. To configure a program to send messages through Tor while in their account, it's easy. Harder to ensure that the program allows you to create through Tor new accounts (if you work in operating system Tails, then you have nothing to worry about, as all your traffic will pass through the Tor network). In this regard, I recommend to choose a Jabber server that will allow you to create a new account from the website, you can do this in Tor browser is a program for messaging.
Here are a few Jabber servers where you can create a new account using the Tor browser. They are selected randomly from the list of public servers: ChatMe (located in Italy), CodeRollers (located in Romania), Darkness XMPP (located in Russia), KodeRoot (located in USA), Jabber.at (located in Austria), Hot-Chilli (located in Germany), XMPP.jp (located in Japan), etc. the List is pretty big.
Ready to get started? Select the Jabber server. Create a username unrelated to your real identity. Create a password that you never use.
Create an account in Jabber using the Tor browser. Now write the data of the server on which you created an account your username and password and proceed to the next section depending on the platform you use: Android, Mac OS X, Windows or Linux.
Select your operating system:
- Anonymous exchange encrypted messages on Android;
- Anonymous exchange encrypted messages on Windows and Linux;
- Anonymous exchange encrypted messages on Mac OS X.
(Yet there is no guide for iOS, as, despite the fact that ChatSecure for iOS has experimental support Tor developers don't recommend you to count on complete anonymity, while experts in the field of security will not conduct a thorough check of the application).
Anonymous transmission of encrypted messages in Mac OS XIf you have not yet created a new account in Jabber using the Tor browser, create it in accordance with the instructions in the section "Choose Jabber server", located above. Make sure you know which server you created your account and your username and password.
For this example I created a account in Jabber server xmpp.jp and get the login pluto1.
Install Adium and configure the anonymous account via Tor,Download and install the Adium client for messaging for Mac, which supports the encryption Protocol OTR.
Make sure the Tor browser is open. While it is open, Tor is running on your computer in the background. When you close the Tor browser, a service Top will also stop their work. This means that every time you want to use your hidden account in Jabber, your Tor browser should be run in the background, otherwise Adium just can't connect. So, open the Tor browser and do not close it until you have completed all instructions.
Open Adium. Once you open this, you will see the window Adium Assistant Wizard. Close: we will create the account manually to get the additional features.

Selecting the window "Contacts" (Contacts), click on the menu bar at the top of Adium and select "Settings" (Preferences). Make sure that the selected tab is "Account" (Accounts) to the top of the window. Click on the "+" button in the bottom left of the window to add a new account. Then in the drop-down list, select "XMPP (Jabber)".

After that will appear a new dialog box where you can set the settings for your account.

Before proceeding to the next step, switch to the tab "Proxy" (Connect using proxy) and select type "SOCKS5". In the "Server" field, enter "127.0.0.1" and the Port box type "9150". Think of this account with a user name and password and enter them in corresponding fields. These settings ensure that Adium will connect to that account through Tor. To enter a user name and password are not required, but if you are going to use them, then Tor will pick up for this account, distinct from other communication channels, which will increase your anonymity.

Go to the tab "Security" (Privacy). In the "Encryption" (Encryption) change the value from "Encrypt messages on request" (Encrypt chats as requested) to "Conduct mandatory encryption to prevent plaintext" (Force encryption and refuse plaintext).

Go to the tab "Settings" (Options). Change the field "Resource" (Resource) (the default name of your computer) to "anonymous". In addition, the item "Security" (Security) check the box next to "Require SSL/TLS" (Require SSL/TLS).

Now go to the tab "Account" (Account). Enter the Jabber ID. Username – pluto1, the server name of the Jabber xmpp.jp, therefore, the Jabber ID will be recorded as pluto1@xmpp.jp. Enter your password and click "OK" to log in to your account.

Now Adium will attempt to connect to your anonymous account through Tor. If all goes well, in the list of accounts should appear in your account with the caption "Online".

Encryption keys and printsso you anonymously included in their hidden account via Tor. Next step is to create the encryption key according to the OTR Protocol. Everyone who wants to use the OTR Protocol must generate a private key. This key is a file stored on the device you use for messaging. Each key contains a unique sequence of characters called a fingerprint of this key: no two keys can have the same fingerprint.
Try to create your key with encryption via the OTR. In the window "Contacts" (Contacts), click on the Adium menu bar and select "Preferences" (Preferences). Go to the "Advanced" tab (Advanced) and click on the sidebar "Encryption" (Encryption). Select the anonymous account and click "Generate" (Generate) button to generate a new key. After the procedure is completed you will have new fingerprint encrypted by OTR.

In our example, I created a new key, using the encryption OTR for your account pluto1@xmpp.jp with the imprint C4CA056C 922C8579 C6856FBB 27F397B3 2817B938. If you want to start with someone personal correspondence, inform that person your login and server name and key fingerprint OTR. After it will create an anonymous account in Jabber and generate a key encrypted with OTR, and ask them to tell you your username, server name and key fingerprint.
After the exchange of encrypted messages, you will be able to see the key fingerprint of his companion, and he will be able to see your. If the print delivered to you, coincides with the imprint that appears in Adium, the contact can be marked as reliable. If the print that gave you matches the fingerprint that is displayed in Adium, then your contact may also be marked as reliable.
This step is somewhat involved, but very important. If the key fingerprint does not match, it means that you are targeted by the attack of a mediator. In this case, do not mark the contact as a reliable, and try to repeat the procedure later.
Adding contacts and personal correspondenceI'm trying to start private messaging with a friend. He told me that his account in Jabber pluto2@wtfismyip.com and OTR-fingerprint – A65B59E4 0D1FD90D D4B1BE9F F9163914 46A35AEE.
After I created my account pluto1, I want to add user pluto2 to his contacts. First, I choose the window "Contacts" (Contacts) and then click on the menu "Contact" and select "Add contact" (Add Contact). In the "Type of contact" (Contact Type) I choose XMPP, and the Jabber ID enter "pluto2@wtfismyip.com". Then click on the "Add" button (Add) to add a user to your contact list.

After you have added a contact in Jabber, you can't immediately determine it is in network or not. First you need to obtain consent to view its status. So now I have to wait until pluto2 enters in to your account and confirm my request to add to contacts.
So pluto2 allowed me to see when he is online, he sends a request to me to let him see when I am online. I choose the contact and click on the "Allow to add me to your list of contacts" (Authorize).

Now I first added user pluto2 as your contact and it will appear in my contact list, when will be online. Then all I need to do to begin with is to double-click on its name.

I clicked twice on the contact pluto2 wrote, "hi."

Before to send my message, Adium started the session with OTR encryption. Note the inscription "personality pluto2@wtfismyip.com not confirmed" (pluto2@wtfismyip.com's identity not verified). This means that during the exchange of encrypted messages I can't be sure that will not happen the attacks of the mediator.
In addition, POPs up a dialog box "Confirm imprint OTR" (OTR Fingerprint Verification box). Does the imprint which gave me the user pluto2, with what is written in this window?

I compare each of the symbols imprint, which pluto2 gave me earlier, with the characters of the thumbprint referenced in Adium. It is seen that they are really the same. So, no one proceeds to attack the encryption, I can press the button "Accept" (Accept). If I didn't have an OTR fingerprint pluto2, I would have asked for it pluto2 external [eng. out-of-band] channel (not in this chat, as I don't know how reliable it is), and then confirmed that they match. If I didn't have time for this, I would have clicked on the button "Confirm later" (Verify Later).
You need to go step confirmation just before the exchange of encrypted messages with the new contact. If tomorrow I go to my account and start a conversation with pluto2, I can immediately start working, considering this conversation is protected.
That's all. The result: we created an anonymous account in Jabber through the Tor network. We set up a program to exchange messages and Adium can log into this account via Tor. We have created a new OTR key encryption for this account. We have added in to your account one contact and checked the print OTR encryption. Now we can share with the contact reports at a high enough level of information protection.published

To be continued...
P. S. And remember, only by changing their consumption — together we change the world! © Join us at Facebook , Vkontakte, Odnoklassniki
Source: habrahabr.ru/company/it-grad/blog/271165/
7 simple recipes for the perfect Breakfast
Forgotten technology of rammed-earth construction for low-rise construction