1031
From the archives declassified NSA
On the official website of the world's largest security services, National Security Agency has a permanent section where from the secret archives for public access regularly uploaded to declassify documents of historical interest. Number of pages in the published materials in such a way intelligence had recently worn vultures SECRET and TOP SECRET, today amounts to many and many thousands. The informative value of the documents, of course, varies very widely, but there are also some real gems.
4 photo

One such material - is an article from the intra-secret NSA Cryptologic Spectrum collection in 1972, which tells about the history of extremely curious complex intelligence technology called "Analysis of side channels of information leakage." This area of technical intelligence, also known under the code word TEMPEST, for many decades, remains one of the biggest mysteries of the security services. Official information on this subject is virtually absent, so that the declassified magazine publication - almost the first in the US reliable evidence obtained, they say, first hand.
When combined with known information previously published in the form of stories, memories of direct participants in the same events in the USSR and the UK, mysterious story TEMPEST gains finally at least some integrity and briefly can be stated about this form.
Home
The first evidence of the attention of experts to the compromising side signals from the equipment, processing information relates to 1943. During the Second World War to encrypt most serious telegraphic communications of the US Army and Navy used the so-called "mixers" manufacture company Bell Telephone. The essence of this structurally simple and at the same time very strong cryptographically Encoder - adding to each character of the plaintext issued by teletype, another sign of a disposable punch tape encrypting key. Mixing these two "jets", a mixer-encoder provides absolute telegram cryptographic protection if signs with a key punch tape random and equally. In other words, the enemy, who was able to intercept the encrypted message, there is no chance to recover the plaintext analytically ... But this is only in theory.
In practice, however, when one of these mixers were tested at Bell Labs, a research engineer accidentally drew attention to an interesting fact. Whenever the unit encrypt the next letter, the oscilloscope across the lab slipped a characteristic burst of signal. To take a more careful study of the structure of these bursts, the engineer was surprised to find that they can restore the shape of the signs in the plaintext message, which encrypts the mixer.
Concerned leadership of Bell had told the military to identify potential threats in their equipment, but the Defense Ministry reacted to this news with extreme skepticism. The world war was raging, and there some feeble, registered only near the encoder electromagnetic signals as a real threat completely perceived.
But engineers Bell persevered, and volunteered to demonstrate in practice the severity of the problem. For the experiment was chosen New York building, which is kriptotsentr US Army. Secluded located in a different building across the street, at a distance of 30 m, engineers recorded the intercepted signals for about an hour. Then, at a cost analysis of the entire 3-4 hours (record time, even for today's high-tech technologies), we were able to recover about 75% of the text of the secret letters, sent kriptotsentrom.
Equally impressive demonstration, of course, produced the military commanders far more impressive. Though with difficulty, they did agree to consider the proposed Bell measures to enhance the protection of the encoders compromising emissions. But once it became clear that in the field of modernization of these are impossible, and each individual unit will have to return to the manufacturer, from this idea immediately refused, deciding to restrict organizational protection measures. Type vigilant inspection area around kriptotsentra within a radius of 70 m ... But when the war ended and began substantially different difficulty peacetime, then the "small" problem of compromising radiation in the United States for a while just forgot.
But in the Soviet Union, in contrast, by 1945 the same as in the ideological sense of the direction of the production of intelligence security services developed very actively. With significantly different, however, a particular specificity. The Soviet leadership then very interested in not only the signals from the encoder, many important conversations of foreigners outside the walls of the diplomatic embassies in Moscow. To solve this problem, the ingenious inventor Leon Theremin in the 1920s created electronic musical instruments and television, and in 1940 a prisoner-sharashka NKVD "Marfino" (immortalized in the novel Solzhenitsyn's "The First Circle"), invented absolutely fantastic bug device.
This product is a miniature, with a diameter of about a pencil, a hollow cylinder of ending with a flexible membrane attached to it a short pin antenna - no electronics, no more at all. Such kind of "bug" carefully built into a luxurious, load masters of fine wood panels depicting the coat of arms of the United States with a bald eagle, and when the opportunity gala event presented by a group of pioneers of this masterpiece of American Ambassador Averell Harriman. Impressed with the gift, he hung it over his desk, and the KGB for many years have acquired a microphone transmitter, stable working directly from the working room of the American ambassador in his permanent residence in Moscow Spaso House.
AANII and the United States.

Bookmark worked extremely well and has been repeated in several other embassies. Soon Leon Theremin technology perfected his system, named "Buran", which allowed to opt out of the implementation of the resonators and eavesdrop on conversations in the rooms on the vibrations of windowpanes, also aimed to modulate the reflection of radio waves. Subsequently, for the same purpose have become more efficient use of lasers.
"Bug" in the wooden panels survived four US ambassadors and could function normally even though a hundred years, but in 1952 it found accidentally tune in transmission wiretapping, one works in Moscow British experts. Although with great difficulty, the employees of the CIA managed to find a bookmark, but for them to remain totally incomprehensible how such a product could work in general - without power, without wires and without electronic components. For a device like an alien technology as a matter of very characteristic name stuck The Thing, that depending on the specific context can be understood as a "thing", "something", "gizmo" or even "bollocks."
To understand the structure helped all those Englishmen. Peter Wright (Peter Wright), leading scientific and technical staff of the British secret service MI5, was able to restore the principle of operation of this "gizmos." Later in MI5 began to make a witty remark as spy gadget that called SATYR used by British and US intelligence services
Mechanism of action:
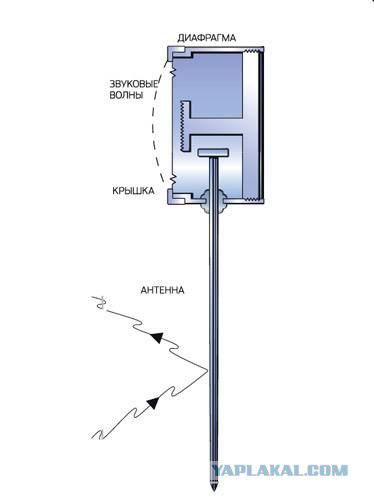
An ingenious invention Theremin resembled a sample of alien technology - without batteries and electronic components.
The secret work of the invention is a passive cavity, is as follows. The building opposite the diplomatic mission was a transmitter emitting in the office of Ambassador unmodulated radio waves with a frequency of 330 MHz.
Under the influence of the external electromagnetic field of the same frequency "bug" has intensified - cylinder chamber to join with him in response and re-emit a radio wave through the antenna-back pin. If in the room there was a conversation, tympanic membrane modulated the re-emission wavelength. Signals take appropriate radio Soviet secret services and recorded on tape.
Secrets for two
Around the same time, in 1951, engineers, researchers have rediscovered the CIA again almost forgotten the effect of compromising electromagnetic radiation from the encoders and shared his discovery with the military signals intelligence (intelligence service, the predecessor of the NSA). Since this time without any problems managed to recover the plaintext message at a distance of about half a kilometer, followed by numerous experiments with the phenomenon in various forms of its manifestation. In the course of these experiments, it was found out that the compromising side signals, and very strongly, produces virtually any equipment, processing information: TTY and phone numbers, encoders and typewriters, copying machines and facsimile machines, not to mention computers.
About the real success of the American intelligence services in this field to this day do not know almost nothing. But a few very successful Tempest attacks English he told Peter Wright in his memoir book "Spycatcher," published in 1987 in Australia, despite the extremely vigorous resistance to the British authorities.
According to Wright, in 1956, during one of the operations, which bore the name Engulf, sensitive microphones secretly installed in the Egyptian embassy in London, the British allowed the sounds of mechanical encoder Hagelin access to secret diplomatic correspondence of the Arabs during the Suez crisis. Other, more technically sophisticated operation Stockade was held against France. In 1960, the British were negotiating to join the European Economic Community, and Prime Minister Macmillan was worried that French President de Gaulle, dissatisfied special relationship with Britain, the United States will block the country's entry into the Community. Therefore, Prime asked scouts to find out the position of France in the negotiations. They tried to break the French diplomatic cipher, but without success. However, Wright and his team noticed that encrypted traffic carried a faint secondary signal, and constructed equipment to recover the signal. It turned out that it was an open text, which somehow leaked through the encoder line ...
By 1964, the intelligence services to cooperate closely in Britain and the United States, it became clear that the Soviet and technical intelligence for all these years is not standing still. The attempt in this period a large sweep in the building of the US embassy in Moscow has identified not only over 40 eavesdropping microphones, but also a lot of new technical devices with unclear principles of work. For example, just above the area kriptotsentra where encoders were treated with a secret diplomatic correspondence of the State Department, it was found hefty metal grill, carefully walled in concrete floor. In other areas showed a smaller lattice - with wires that went into the wall and lead to God knows where. There were also found a piece of wire, which had, however, at the end of the load mesh jewelry from a microscopically thin wires as thick as a hair. Equally mysterious discoveries are continually being discovered in the US Embassy in Prague, Budapest and Warsaw.
one of the decoders Hagelin

Thing to all
Although, as you can see by the middle of 1960 Tempest intelligence operations already had quite a mature character and a very impressive scale, the level of secrecy was such that the general public knows nothing about the side channels to compromise the mid-1980s. Then came the independent rediscovery of these principles by scientists and engineers, not related to state secrets. And now the opening accompanied by the relevant publication of the results in popular articles and spectacular public demonstrations "spy technology", sometimes very similar to the focus or draw.
The first important result was obtained in 1985, when a Dutch computer engineer Wim van Eck, engaged in medical technology, in the course of the experiments found that by using the TV antenna and manually configure the clock generator can be remotely restore the image of another video display - even if that works another building. Article van Eck in the journal Computers & Security and spectacular five-minute demonstration of his "spy" on television technology, the transfer of BBC BBC "World of Tomorrow" had a very big resonance in the world of scientists and engineers. For several years an open academic community were pereobnaruzheny almost all the main channels by leaks of information - both electromagnetic (especially the connecting cables) and acoustic (for example, from the sounds of button presses keyboard).
Inquiring researchers in university laboratories independently discovered new, highly original channels leaks. So, working at Cambridge German scientist Markus Kuhn in 2002 showed that in principle it is possible to restore the image on the TV screen or computer monitor only one flicker of light in the room - from a distance of several hundred meters. Kuhn for this required good optical tube, high-quality light sensor, and a thorough understanding of the intricacies of cathode ray tubes.
Around the same time the American researcher Joe Locri showed that with decent optics and light sensor can be at a distance of 1, 5 km to take data from the flashing lights indicator of computer equipment. It was found that the modem connected to the PC network, LED blinking exactly corresponds to the bits of information passing through a computer.
Now the topic of side channel leakage also often mentioned in connection with open new ways hackers compromise smartcards. In the late 1990s, it was demonstrated that through the analysis of fluctuations in the power supply smartkartnyh processors can be removed from their encryption keys that protect the most important information. This famous work of American Paul Kocher has inspired a number of deep Tempest Research in the cryptographic community, resulting in the show, in particular, that such an attack by using directional radio antenna can be remotely retrieve keys from specialized kriptoakseleratorov which servers companies provide uskorennnuyu processing encrypted financial transactions involving bank credit cards ...
One of the most prominent security experts in their comments on all these works reasonably pointed out that the main secret of "Tempest" as a nuclear bomb, was the fact of the possibility of technology. When this fact became common knowledge, set by the major channels of information leakage can be any competent engineer.
Author: Kiwi Bird
Source:
4 photo

One such material - is an article from the intra-secret NSA Cryptologic Spectrum collection in 1972, which tells about the history of extremely curious complex intelligence technology called "Analysis of side channels of information leakage." This area of technical intelligence, also known under the code word TEMPEST, for many decades, remains one of the biggest mysteries of the security services. Official information on this subject is virtually absent, so that the declassified magazine publication - almost the first in the US reliable evidence obtained, they say, first hand.
When combined with known information previously published in the form of stories, memories of direct participants in the same events in the USSR and the UK, mysterious story TEMPEST gains finally at least some integrity and briefly can be stated about this form.
Home
The first evidence of the attention of experts to the compromising side signals from the equipment, processing information relates to 1943. During the Second World War to encrypt most serious telegraphic communications of the US Army and Navy used the so-called "mixers" manufacture company Bell Telephone. The essence of this structurally simple and at the same time very strong cryptographically Encoder - adding to each character of the plaintext issued by teletype, another sign of a disposable punch tape encrypting key. Mixing these two "jets", a mixer-encoder provides absolute telegram cryptographic protection if signs with a key punch tape random and equally. In other words, the enemy, who was able to intercept the encrypted message, there is no chance to recover the plaintext analytically ... But this is only in theory.
In practice, however, when one of these mixers were tested at Bell Labs, a research engineer accidentally drew attention to an interesting fact. Whenever the unit encrypt the next letter, the oscilloscope across the lab slipped a characteristic burst of signal. To take a more careful study of the structure of these bursts, the engineer was surprised to find that they can restore the shape of the signs in the plaintext message, which encrypts the mixer.
Concerned leadership of Bell had told the military to identify potential threats in their equipment, but the Defense Ministry reacted to this news with extreme skepticism. The world war was raging, and there some feeble, registered only near the encoder electromagnetic signals as a real threat completely perceived.
But engineers Bell persevered, and volunteered to demonstrate in practice the severity of the problem. For the experiment was chosen New York building, which is kriptotsentr US Army. Secluded located in a different building across the street, at a distance of 30 m, engineers recorded the intercepted signals for about an hour. Then, at a cost analysis of the entire 3-4 hours (record time, even for today's high-tech technologies), we were able to recover about 75% of the text of the secret letters, sent kriptotsentrom.
Equally impressive demonstration, of course, produced the military commanders far more impressive. Though with difficulty, they did agree to consider the proposed Bell measures to enhance the protection of the encoders compromising emissions. But once it became clear that in the field of modernization of these are impossible, and each individual unit will have to return to the manufacturer, from this idea immediately refused, deciding to restrict organizational protection measures. Type vigilant inspection area around kriptotsentra within a radius of 70 m ... But when the war ended and began substantially different difficulty peacetime, then the "small" problem of compromising radiation in the United States for a while just forgot.
But in the Soviet Union, in contrast, by 1945 the same as in the ideological sense of the direction of the production of intelligence security services developed very actively. With significantly different, however, a particular specificity. The Soviet leadership then very interested in not only the signals from the encoder, many important conversations of foreigners outside the walls of the diplomatic embassies in Moscow. To solve this problem, the ingenious inventor Leon Theremin in the 1920s created electronic musical instruments and television, and in 1940 a prisoner-sharashka NKVD "Marfino" (immortalized in the novel Solzhenitsyn's "The First Circle"), invented absolutely fantastic bug device.
This product is a miniature, with a diameter of about a pencil, a hollow cylinder of ending with a flexible membrane attached to it a short pin antenna - no electronics, no more at all. Such kind of "bug" carefully built into a luxurious, load masters of fine wood panels depicting the coat of arms of the United States with a bald eagle, and when the opportunity gala event presented by a group of pioneers of this masterpiece of American Ambassador Averell Harriman. Impressed with the gift, he hung it over his desk, and the KGB for many years have acquired a microphone transmitter, stable working directly from the working room of the American ambassador in his permanent residence in Moscow Spaso House.
AANII and the United States.

Bookmark worked extremely well and has been repeated in several other embassies. Soon Leon Theremin technology perfected his system, named "Buran", which allowed to opt out of the implementation of the resonators and eavesdrop on conversations in the rooms on the vibrations of windowpanes, also aimed to modulate the reflection of radio waves. Subsequently, for the same purpose have become more efficient use of lasers.
"Bug" in the wooden panels survived four US ambassadors and could function normally even though a hundred years, but in 1952 it found accidentally tune in transmission wiretapping, one works in Moscow British experts. Although with great difficulty, the employees of the CIA managed to find a bookmark, but for them to remain totally incomprehensible how such a product could work in general - without power, without wires and without electronic components. For a device like an alien technology as a matter of very characteristic name stuck The Thing, that depending on the specific context can be understood as a "thing", "something", "gizmo" or even "bollocks."
To understand the structure helped all those Englishmen. Peter Wright (Peter Wright), leading scientific and technical staff of the British secret service MI5, was able to restore the principle of operation of this "gizmos." Later in MI5 began to make a witty remark as spy gadget that called SATYR used by British and US intelligence services
Mechanism of action:
An ingenious invention Theremin resembled a sample of alien technology - without batteries and electronic components.
The secret work of the invention is a passive cavity, is as follows. The building opposite the diplomatic mission was a transmitter emitting in the office of Ambassador unmodulated radio waves with a frequency of 330 MHz.
Under the influence of the external electromagnetic field of the same frequency "bug" has intensified - cylinder chamber to join with him in response and re-emit a radio wave through the antenna-back pin. If in the room there was a conversation, tympanic membrane modulated the re-emission wavelength. Signals take appropriate radio Soviet secret services and recorded on tape.

Secrets for two
Around the same time, in 1951, engineers, researchers have rediscovered the CIA again almost forgotten the effect of compromising electromagnetic radiation from the encoders and shared his discovery with the military signals intelligence (intelligence service, the predecessor of the NSA). Since this time without any problems managed to recover the plaintext message at a distance of about half a kilometer, followed by numerous experiments with the phenomenon in various forms of its manifestation. In the course of these experiments, it was found out that the compromising side signals, and very strongly, produces virtually any equipment, processing information: TTY and phone numbers, encoders and typewriters, copying machines and facsimile machines, not to mention computers.
About the real success of the American intelligence services in this field to this day do not know almost nothing. But a few very successful Tempest attacks English he told Peter Wright in his memoir book "Spycatcher," published in 1987 in Australia, despite the extremely vigorous resistance to the British authorities.
According to Wright, in 1956, during one of the operations, which bore the name Engulf, sensitive microphones secretly installed in the Egyptian embassy in London, the British allowed the sounds of mechanical encoder Hagelin access to secret diplomatic correspondence of the Arabs during the Suez crisis. Other, more technically sophisticated operation Stockade was held against France. In 1960, the British were negotiating to join the European Economic Community, and Prime Minister Macmillan was worried that French President de Gaulle, dissatisfied special relationship with Britain, the United States will block the country's entry into the Community. Therefore, Prime asked scouts to find out the position of France in the negotiations. They tried to break the French diplomatic cipher, but without success. However, Wright and his team noticed that encrypted traffic carried a faint secondary signal, and constructed equipment to recover the signal. It turned out that it was an open text, which somehow leaked through the encoder line ...
By 1964, the intelligence services to cooperate closely in Britain and the United States, it became clear that the Soviet and technical intelligence for all these years is not standing still. The attempt in this period a large sweep in the building of the US embassy in Moscow has identified not only over 40 eavesdropping microphones, but also a lot of new technical devices with unclear principles of work. For example, just above the area kriptotsentra where encoders were treated with a secret diplomatic correspondence of the State Department, it was found hefty metal grill, carefully walled in concrete floor. In other areas showed a smaller lattice - with wires that went into the wall and lead to God knows where. There were also found a piece of wire, which had, however, at the end of the load mesh jewelry from a microscopically thin wires as thick as a hair. Equally mysterious discoveries are continually being discovered in the US Embassy in Prague, Budapest and Warsaw.
one of the decoders Hagelin

Thing to all
Although, as you can see by the middle of 1960 Tempest intelligence operations already had quite a mature character and a very impressive scale, the level of secrecy was such that the general public knows nothing about the side channels to compromise the mid-1980s. Then came the independent rediscovery of these principles by scientists and engineers, not related to state secrets. And now the opening accompanied by the relevant publication of the results in popular articles and spectacular public demonstrations "spy technology", sometimes very similar to the focus or draw.
The first important result was obtained in 1985, when a Dutch computer engineer Wim van Eck, engaged in medical technology, in the course of the experiments found that by using the TV antenna and manually configure the clock generator can be remotely restore the image of another video display - even if that works another building. Article van Eck in the journal Computers & Security and spectacular five-minute demonstration of his "spy" on television technology, the transfer of BBC BBC "World of Tomorrow" had a very big resonance in the world of scientists and engineers. For several years an open academic community were pereobnaruzheny almost all the main channels by leaks of information - both electromagnetic (especially the connecting cables) and acoustic (for example, from the sounds of button presses keyboard).
Inquiring researchers in university laboratories independently discovered new, highly original channels leaks. So, working at Cambridge German scientist Markus Kuhn in 2002 showed that in principle it is possible to restore the image on the TV screen or computer monitor only one flicker of light in the room - from a distance of several hundred meters. Kuhn for this required good optical tube, high-quality light sensor, and a thorough understanding of the intricacies of cathode ray tubes.
Around the same time the American researcher Joe Locri showed that with decent optics and light sensor can be at a distance of 1, 5 km to take data from the flashing lights indicator of computer equipment. It was found that the modem connected to the PC network, LED blinking exactly corresponds to the bits of information passing through a computer.
Now the topic of side channel leakage also often mentioned in connection with open new ways hackers compromise smartcards. In the late 1990s, it was demonstrated that through the analysis of fluctuations in the power supply smartkartnyh processors can be removed from their encryption keys that protect the most important information. This famous work of American Paul Kocher has inspired a number of deep Tempest Research in the cryptographic community, resulting in the show, in particular, that such an attack by using directional radio antenna can be remotely retrieve keys from specialized kriptoakseleratorov which servers companies provide uskorennnuyu processing encrypted financial transactions involving bank credit cards ...
One of the most prominent security experts in their comments on all these works reasonably pointed out that the main secret of "Tempest" as a nuclear bomb, was the fact of the possibility of technology. When this fact became common knowledge, set by the major channels of information leakage can be any competent engineer.
Author: Kiwi Bird
Source:























