1545
The more dangerous "smart" power
98,185,012
Electricity is expensive, and the global economy hard looking for ways to improve their energy efficiency. In addition to solar and wind power plants in the world is an active construction of "smart" electricity distribution networks, so-called Smart Grid, which allow to use energy rationally. They are usually automated and connected to the Internet, causing a natural interest in their level of security.
Warning! All described in Article vulnerability transferred to manufacturers and they are eliminated, but can occur in operating systems
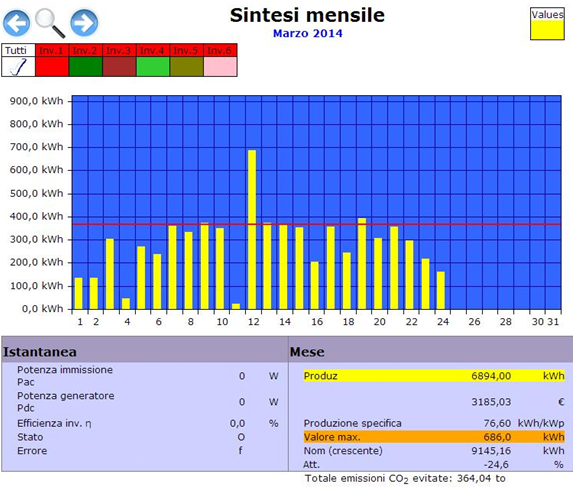
What are they made h4> Technology Smart Grid just getting ready to conquer the world. Now they are used mainly in household automatic climate control system, which introduced the simplest elements of "smart" grids. Such devices allow the end user to monitor and effectively use wind and solar energy, and in their absence to move to other sources. Dangerous if Smart Grid for progressive homeowners? To answer this question, we need to learn from some of the control components comprise such networks.
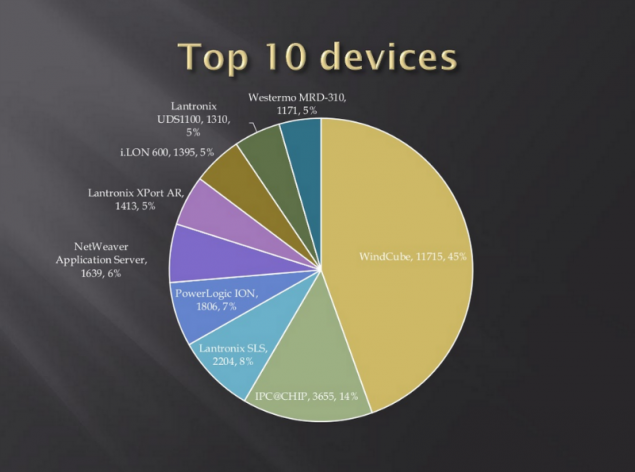
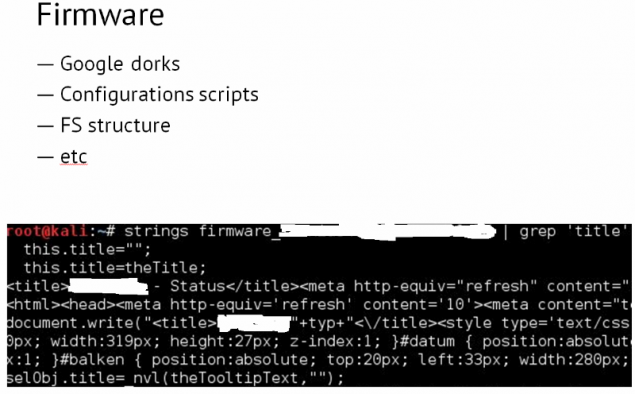
Parse firmware Solar Sail h4>
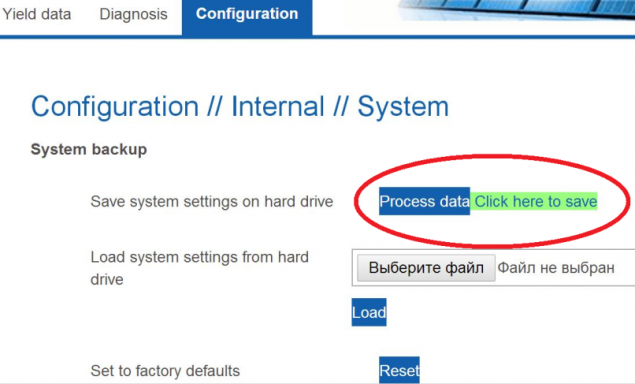
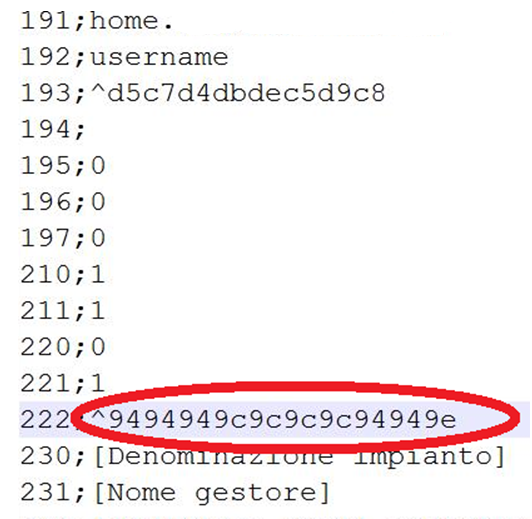
You can and no password h4> More interesting things were found in the admin panel. When studying adminok Solar Sail transpired interesting fact about 5% of systems do not require a password to login to the configuration page. The remaining 95% of the system password has been set, but the sense of it was not enough. Forming a simple query to a single configuration script, you can make the admin panel Solar Sail calmly give the backup configuration, download it to their local computer and remove the password.
Go ahead h4> To get to the configuration page, Solar Sail, as we can see, it turned out quite easy. From this page you can load the firmware of the device where to look in her curious artifacts. Incidentally, in the official documentation Solar Sail stated that the firmware update is password protected. However, we are faced with the need to enter the password only on one system, and it was very simple («Solar Sail»), coincided with the login and was unavailable for changing the normal user.
What's tomorrow? H4> Members 'smart homes' and mini offices connected to alternative energy sources, appear, in fact, beta testers systems Smart Grid. And developers are not spared too thrifty owners, allowing serious errors in the protection mechanism. In our case, anyone could choose one of the hundreds of thousands of owners of units Smart Grid Solar Sail from the Internet to bypass authentication (sometimes it is not required) to remotely install the defective firmware seize access to control parameters of the system, get into the other network segments. Possible physical effects, up to incapacitate inverters, fire and other unpleasant events.
Electricity is expensive, and the global economy hard looking for ways to improve their energy efficiency. In addition to solar and wind power plants in the world is an active construction of "smart" electricity distribution networks, so-called Smart Grid, which allow to use energy rationally. They are usually automated and connected to the Internet, causing a natural interest in their level of security.
Warning! All described in Article vulnerability transferred to manufacturers and they are eliminated, but can occur in operating systems