1134
SMS-vulnerability in all Nexus
Last Friday at the conference DefCamp Security Conference researcher Bogdan Alecu demonstrated serious vulnerability, which he found in all smartphones Nexus. With its help, the attacker can force the smartphone reboot or cause problems for some services.
Attack is sending several so-called Class 0 «Flash» messages to the target phone. Such "fast" messages are typically used by emergency services and they immediately appear on the screen, bypassing the standard application to handle SMS. Upon receipt of such communication is no sound, but the screen remains one window of this message. The problem is that getting 20-30 of these messages causes an overload of the system. Most often, this translates into the fact that the smartphone stops responding or restarts, in some cases falls Messages app itself or even buggy service responsible for cellular communication.
It is interesting that Alec notified Android Security Team of the vulnerability of a year ago, but initially only received an automated response. Further attempts to contact the responsible specialists were unsuccessful, and he decided to publish the information. Now he and Michael Mueller Class0Firewall developed to combat this threat.
He also notes that his attack until only leads to failures, but in theory can be used for remote code execution.
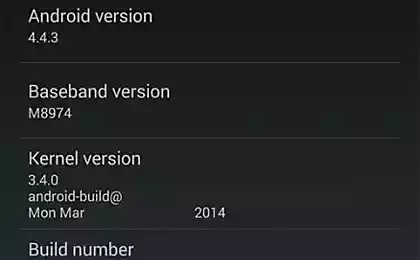
Vulnerability works on all Nexus with default Android, up to version KitKat.
Source: habrahabr.ru/company/apps4all/blog/204428/
Attack is sending several so-called Class 0 «Flash» messages to the target phone. Such "fast" messages are typically used by emergency services and they immediately appear on the screen, bypassing the standard application to handle SMS. Upon receipt of such communication is no sound, but the screen remains one window of this message. The problem is that getting 20-30 of these messages causes an overload of the system. Most often, this translates into the fact that the smartphone stops responding or restarts, in some cases falls Messages app itself or even buggy service responsible for cellular communication.
It is interesting that Alec notified Android Security Team of the vulnerability of a year ago, but initially only received an automated response. Further attempts to contact the responsible specialists were unsuccessful, and he decided to publish the information. Now he and Michael Mueller Class0Firewall developed to combat this threat.
He also notes that his attack until only leads to failures, but in theory can be used for remote code execution.
Vulnerability works on all Nexus with default Android, up to version KitKat.
Source: habrahabr.ru/company/apps4all/blog/204428/