1992
Quantum money
Recently, the hype about the quantum компьютеров (точек, телепортов), in my opinion, lost one small but very important detail, namely quality i> a new mechanism. The world expects from quantum computers unheard of speed (that взломать RSA ), but it's same i> performance, only faster, from quantum dots - high resolution (for you to watch anime), the same pixels / phosphor, only even less; telepotatsiya - same most otovolokno / OWC only faster (of course, I'm oversimplifying).
But back in 1969 (before Feynman, Reed , Minin , Benioff, Deutsch , Yekimova ) proposed the idea of a crank, which can form the basis for future infrastructure information exchange.
In his article, «Conjugate coding» , which he wrote in 1969 and published it only in 1983, Stephen Wiesner proposed the idea of how to protect against counterfeit money .
What is most appealing about the idea of quantum authentication that it is not based on complexity i> (technical, computing, engineering, mathematics, etc.), and on the physical impossible i>. Habré was a wonderful overview «Technique for Authentication of money» , where, in addition to optical, electrical, mechanical, etc. methods of protection, casual mentioned quantum money. (With слабыми measurements yet little is clear, therefore, they are not a threat Quantum money)
"I did not get any support from his supervisor - he never showed any interest in her, I showed her a few more people - they do strange faces, and they returned to his studies.»
Stephen Wiesner, author of the idea of quantum money
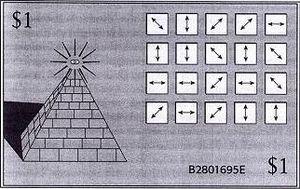
In the picture i>: Quantum bill, proposed by Stephen Vicnerom in 1969. Contains a pyramid with the eye, the serial number and 20 traps photons whose content is a mystery. Each trap is 1 photon with unknown polarization.
At the moment, the idea of quantum realizable money, maybe not yet built a trap for the individual photons. But security experts already in all the proposed protocol and the attack on them.
A theorem on the prohibition of cloning h4>
The polarization of photons h4>
Quantum protection against forgery h4> The database bank contains a pair of "serial number - the polarization of photons." If the bill bank checks, he knows what each photon polarization, and can verify it with a single attempt. In the case of 100% satisfaction - a genuine banknote. And the bank fills' spent photons "again.
Attack and modification of the algorithm h4>
qubits h4> The task of creating quantum memory remains unsolved, but scientists and engineers quietly carved prototypes
About Stephen Wiesner h4> Born in 1942 years, earned a degree in Брандейском University .
But back in 1969 (before Feynman, Reed , Minin , Benioff, Deutsch , Yekimova ) proposed the idea of a crank, which can form the basis for future infrastructure information exchange.
In his article, «Conjugate coding» , which he wrote in 1969 and published it only in 1983, Stephen Wiesner proposed the idea of how to protect against counterfeit money .
What is most appealing about the idea of quantum authentication that it is not based on complexity i> (technical, computing, engineering, mathematics, etc.), and on the physical impossible i>. Habré was a wonderful overview «Technique for Authentication of money» , where, in addition to optical, electrical, mechanical, etc. methods of protection, casual mentioned quantum money. (With слабыми measurements yet little is clear, therefore, they are not a threat Quantum money)

"I did not get any support from his supervisor - he never showed any interest in her, I showed her a few more people - they do strange faces, and they returned to his studies.»
Stephen Wiesner, author of the idea of quantum money
In the picture i>: Quantum bill, proposed by Stephen Vicnerom in 1969. Contains a pyramid with the eye, the serial number and 20 traps photons whose content is a mystery. Each trap is 1 photon with unknown polarization.
At the moment, the idea of quantum realizable money, maybe not yet built a trap for the individual photons. But security experts already in all the proposed protocol and the attack on them.
A theorem on the prohibition of cloning h4> 

Теорема to ban cloning -approving quantum theory of the impossibility of creating a perfect copy of an arbitrary unknown quantum state. The theorem was formulated Vuttersom, Zurek and DIEKS in 1982 and had a great importance in the field of quantum computing, quantum information theory and related fields.
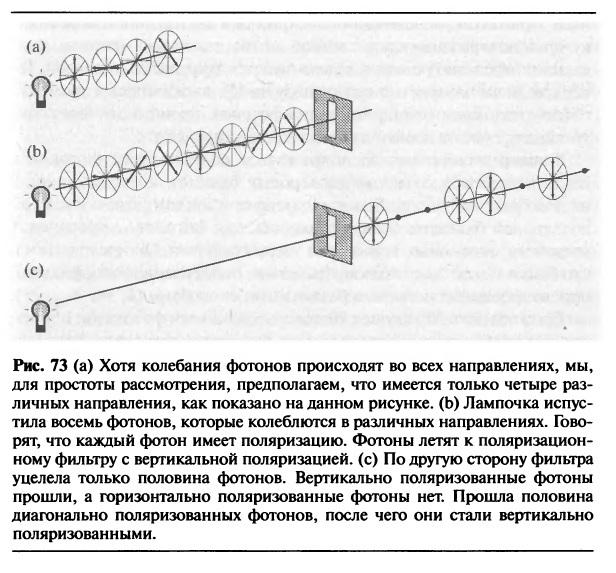
The polarization of photons h4> 
Simon Singh explains the polarization of photons & lt; & lt; on matches & gt; & gt; 

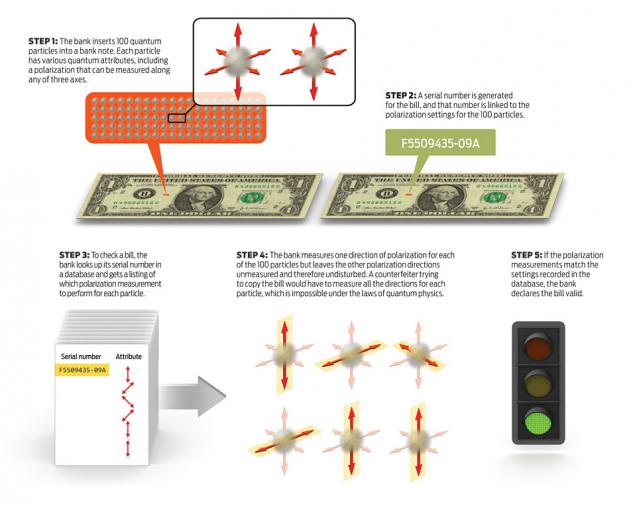
Quantum protection against forgery h4> The database bank contains a pair of "serial number - the polarization of photons." If the bill bank checks, he knows what each photon polarization, and can verify it with a single attempt. In the case of 100% satisfaction - a genuine banknote. And the bank fills' spent photons "again.
An attacker, if he wants to make a duplicate bill or will fill the photons at random, then it turns out that, or he would have to consider the state of the photons. But since each photon him "given 1 attempt," and then the photon is "lost", the attacker does not possess complete information about the photon, and if he would "forge a photon," he made a mistake with a certain probability, and the bank then it can determine. Number of traps for the photon reaches the desired probability of error for us attacker. (The probability of a successful backup does not exceed (5/6) n sup>, where n - number of photons in the bill)
Illustrative algorithm counterfeit protection for 100 photons
Attack and modification of the algorithm h4> 
In the proposed algorithm, Wisner was a lot of shortcomings, such as interference (which forced to abandon a 100% satisfaction and to agree to 90 % compliance), or excessive power , which receives the issuing bank.
But a group of authors from MIT offers its decision .
And this year, went on to become yet another method of attack An adaptive attack on Wiesner's quantum money based on interaction-free measurement
qubits h4> The task of creating quantum memory remains unsolved, but scientists and engineers quietly carved prototypes
Qubit in the lab looks like
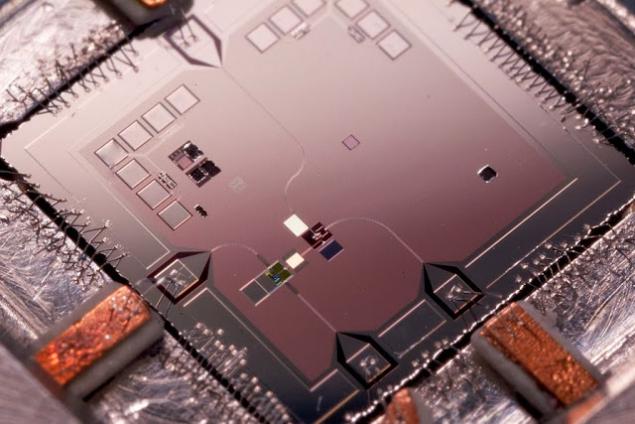
or so
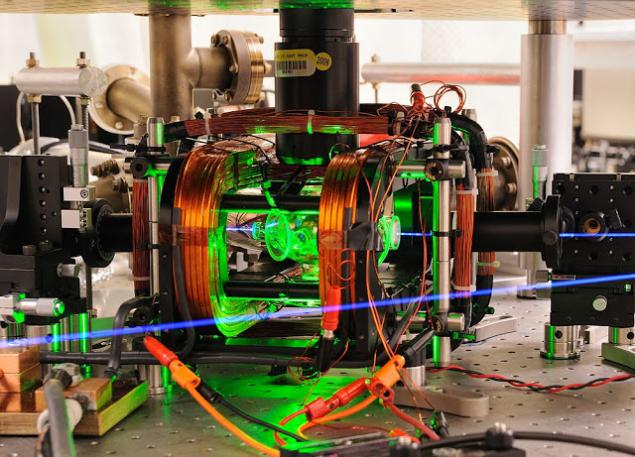
About Stephen Wiesner h4> Born in 1942 years, earned a degree in Брандейском University .
Son Director MIT, advisor to several presidents Science Jerome Wiesner , a keen advocate of unmanned space programs (programs condemned Аполлон, Меркурий and Джемини)
In his article, «Conjugate Coding», Stephen suggested primitive «multiplexing» - which served as the prototype for the record забывчивой transmission .
Wisner co Квантового superdense coding .
Steve Jobs was the starting point for many researchers, including the fathers of quantum cryptography - Charles H. Bennett and Gilles Brassard .
Now Wisner works with team in Israel.
«Looking back, I think if I could have done more of this. People judge me for what I did not put any extra effort to publish their ideas; and I believe that they are in some way wrong, but I was a young graduate student, and to me there was not much confidence. In any case, the quantum of money no one was interested. "
Stephen Wiesner blockquote>
PS. H4>
P.P.S. H4> Purse Schrodinger not know if there is money or not until you open.
The denomination Geyzinberga: you can find one of two things - either the denomination or the authenticity of banknotes.
«codebook. The Secret History of ciphers and their transcripts », Simon Singh
Article about Wiesner in the English-language Wikipedia en.wikipedia.org/wiki/Stephen_Wiesner
Article «Quantum money» in the English-language Wikipedia en.wikipedia.org/wiki/Quantum_money
The article "Quantum money" in the Russian-language Wikipedia ru.wikipedia.org/wiki/Квантовые_деньги
Profile of Stephen Wiesner in LinkedIn www.linkedin.com/pub/steve-wiesner/2a/937/456
Article in Computerra «The new concept of quantum of money»
Article Wiesner «Communication via one- and two-particle operators on Einstein-Podolsky-Rosen states» 1992
Article Wiesner «Conjugate Coding» , 1983
Article «Breaking and making quantum money: toward a new quantum cryptographic protocol»
Post written specifically for the corporate blog Web-payment.ru
Source: habrahabr.ru/company/web_payment_ru/blog/229699/