1230
9 tips from Edward Snowden on how to protect themselves online
Probably everyone at least once thought about how to protect themselves online. Even schoolboys know that browsers, social networks and the kinds of programs collect information about users, but few know how to avoid it.
We are in the Website don't want to followed us, so he gathered tips from a former CIA officer Edward Snowden about how to make Internet surfing and data storage safer.

Sites with an encrypted connection

Many people believe that they have nothing to hide. They believe that agents care about the information on where they were, what they shared on their Facebook page and purchased on Ebay. And they are right. But this position involves another aspect of the problem.
"When you say "I have nothing to hide," you say "I don't care about my Internet security, I agree that they're watching me". Edward Snowden
Edward Snowden advises not to throw so simple their rights and to visit only those sites that use an encrypted connection. These are the sites that begin with https. Attackers can steal your official documents, business correspondence, family photographs, and their fate will be unpredictable. So treat this matter with seriousness. To check whether or not you have a connection, you can install a special plugin that will automatically encrypt all the websites that you visit.
Correspondence

You are chatting or sending my friends pictures of their children? All of this could fall into the wrong hands. If you want to protect yourself, install a special extension — cipher for your browser. It works quite simple: you send a message and the recipient receives it in encrypted characters. To decrypt the message, it must enter a special key. Just don't send the key esemeski or message in a social network. Better tell him in person or send with the help of a program that uses encryption.
Messengers

Attackers often attacking the messengers. First and foremost, to protect yourself, use instant messengers, which automatically encrypts correspondence, such as Telegram, WhatsApp, Facebook Messenger, Signal Private Messenger, etc. If someone intercepts your conversation, you'll see only the character set for the decoding of which will take more time than human life. But out of curiosity, the company that owns the messenger, it won't protect: the companies usually have the keys to read your chats, and if anything they can provide it to law enforcement.
To avoid this, use the messenger with connected plug-in for encryption in the process of sending a message. Such a plugin is often called OTR: off the record — prevents the record. For Example, RedPhone.
Insecure about the "cloud"

Cloud storage is also unsafe. Google Drive, Dropbox, OneDrive, iCloud — all this is vulnerable to attackers who can guess the password or use the vulnerability of the system. In order to keep their data secret, use a program that encrypts them. Such programs create a folder on your computer, you put the files there, they are automatically encrypted and sent to cloud storage. For example, you can set the program Boxcryptor, it is free for personal use.
Secret browser

If you have to use an unencrypted Wi-Fi in a public place, encrypt all traffic (not only browser). To do this is to use a VPN simply put, it's a encrypted channel, to extend from you to your VPN provider. On the provider's server, traffic is decrypted and sent on to the destination. You can use the services of free providers, for example, or VPNbook Freevpn. Thanks to this connection will give the impression that you surf the web with VPN server and not from your computer.
You can install the TOR browser — when it is properly configured, no one can know where you are and who you are.
Telephone

Encrypt flash drives, phones and other things that you can lose. To do this, use simple encoding program that you can download online. Typically, these programs work behind the scenes, that is, encrypt and decrypt files automatically. If encrypted, the device will fall into the hands of the attacker, he can't do anything out again.
For full encryption of smartphones and tablets it is better to use built-in functionality of the operating system. On Android devices, look in "Settings -> Security" on iOS in "Settings -> Password".
Personal conversations
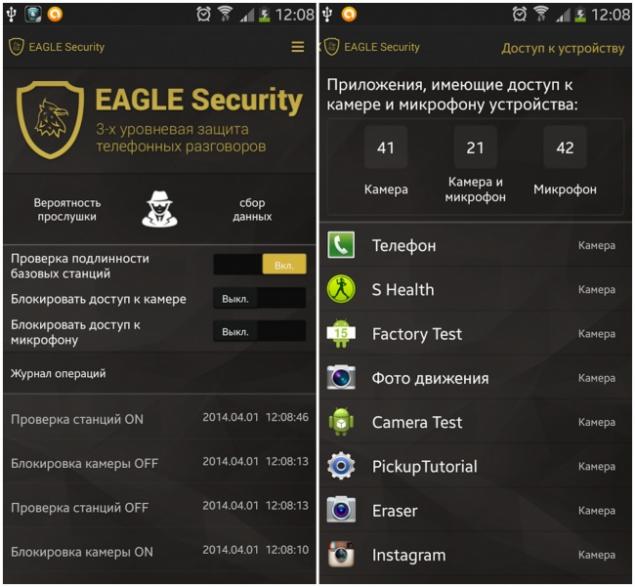
As you know, almost any phone you can listen to. To your personal conversation is not recognized any more, there are special applications such as EAGLE Security. These applications keep track of and remember the location of all base stations. If they discover that some base moves across town or the signal from time to time disappears from its location, they mark it as false and suspicious and notify the owner of the phone. In such programs it is usually possible to see which installed on your phone apps have access to camera and microphone and turn them off.
Insidious is

Viruses spyware can pretend to be a conventional advertising. Not to get hooked on criminals install on your computer blocking advertising. And always update software, especially antivirus software.
A good password is the key to the success of

Think of complex passwords. Simple words, sequence numbers, date of birth, your name and the name of his pet is the most unreliable passwords. A good password consists of uppercase and lowercase letters, numbers, and punctuation. It is also important to think of different passwords for websites, mail and social networks. Otherwise, the hacking of your account password can be used by hackers and other resources.
Think twice before you tell something about yourself in a public space.
See also
How to disappear from the Internet
7 good reasons why you should not post pictures of their children online
via www.adme.ru/zhizn-semya/7-veskih-prichin-pochemu-ne-stoit-razmeschat-fotografii-svoih-detej-v-internete-1326365/
15 of the most striking beauty Queens in the entire history of the contest "Miss world"
14 coolest short series that you could accidentally miss