Dangerous virus LLC Mail.Ru, walking across the expanses of the RuNet
 Bashny.Net
Bashny.Net
In the expanses of the Internet is walking a dangerous new computer virus with a signature
LLC Mail.Ru, which masquerades as an update of popular programs.
Be vigilant, comrades.
Many Internet users have noticed strange messages in a variety of applications that offer to install or upgrade version of the popular program.
Today I want to tell you about the banal update the Skype.
After confirmation by the user update from the infected source
downloaded and installed "update", but when he saw after the launch,
that the file is signed by the publisher somehow «LLC Mail.Ru», instead of Skype,
I advise you to immediately ban the execution of the task.
Read more about the fresh filling botnet scheme.
In most cases, after clicking on the "software update" comes redirect
to boot from the infected sites by type _http: // «any site name» / skype /,
looking something like this ...

"Your version of Skype, LLC, its support will end 04.03.2013,
then you will not be able to communicate by Skype »it is very frightening,
Riddle signature
So, first of all look at the file properties:
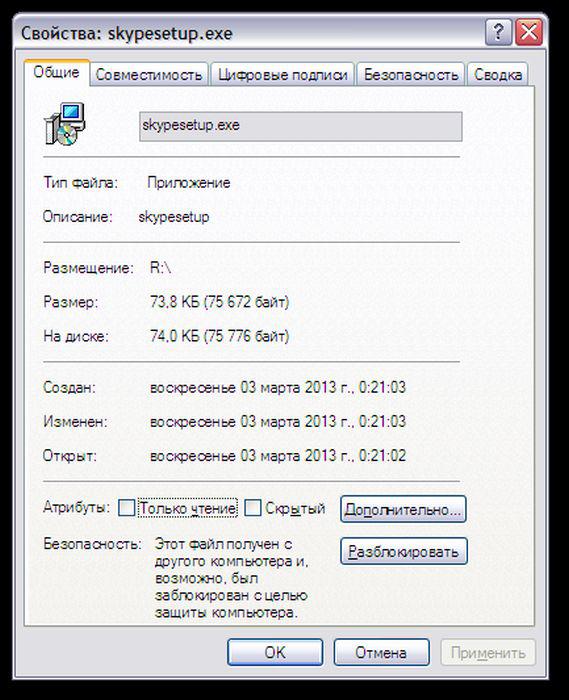
Strangely, only 74 KB, once is not enough even for web-installer.
Enjoying a digital signature, what is this «LLC Mail.Ru» is,
can someone again dragged through the legal entity Thawte similar name?
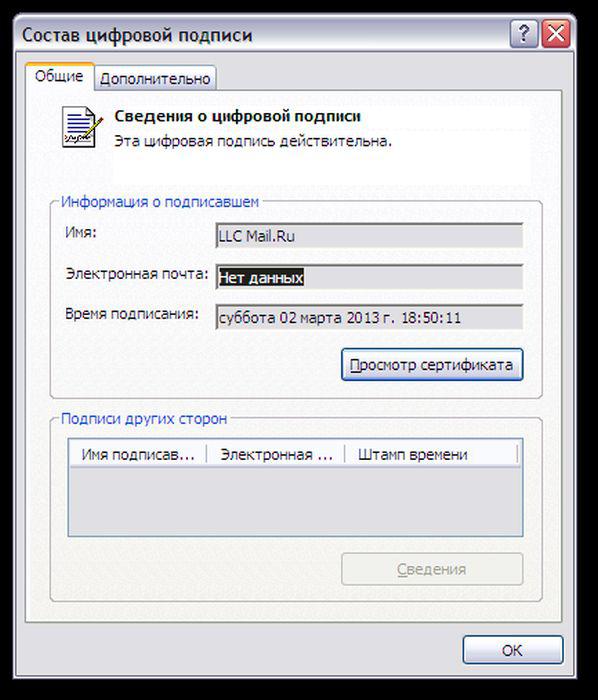
Strangely, the digital signature certificate is very similar to this from the Mail.Ru:
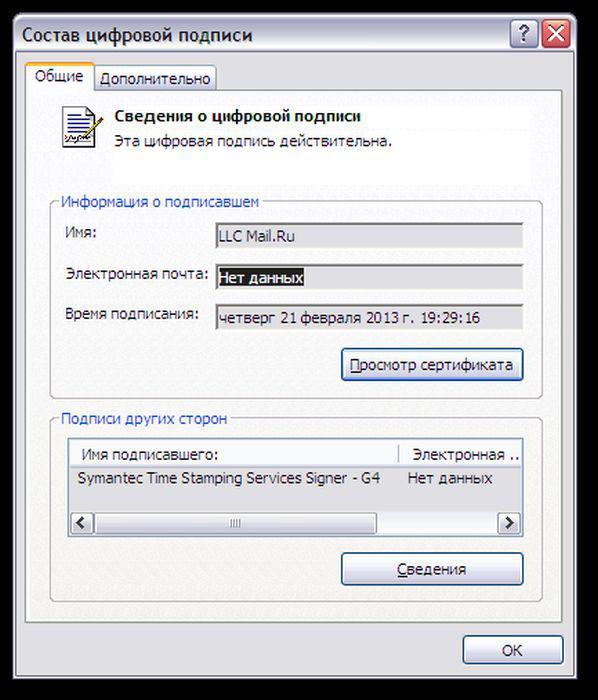
They have the same validity period of 02.07.2014 to 09.12.2011, but
in a digital signature has a signature Agent Mail.ru others:
Symantec Time Stamping Services Signer. All exe files are signed
on the fly before giving the browser to download,
This is evidenced by dynamically changing the time of signature file.
Total, we have three options:
1. This is a real digital signature Mail.ru, a private key from which
somehow stolen and now is used for signing Malvar
2. This is a real digital signature Mail.ru, which itself Mail.ru any reason
uses for signature Malvar
3. It is a fake digital signature Mail.ru, which is in any way
We were able to compromise (which is unlikely, since RSA 2048 bits)
Zaguglit source that is most often used by hackers - «easyupdate.ru»,
and did not find anything worthwhile to issue, I looked at all the links on demand site: easyupdate.ru
and found that, in addition to Skype, Landing are available for all popular browsers:
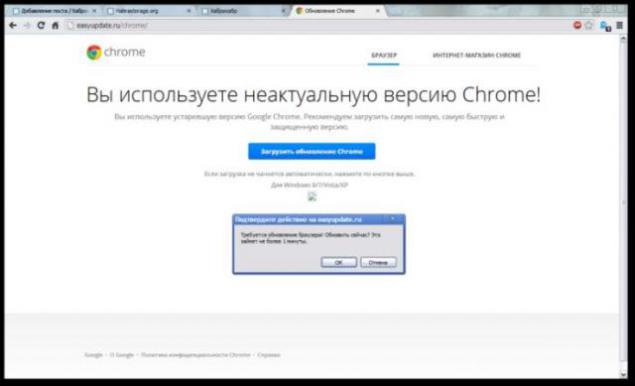
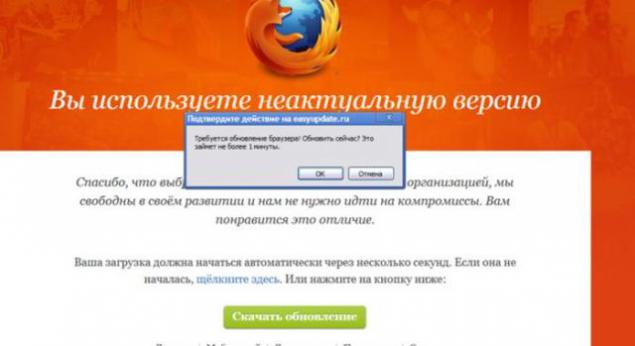
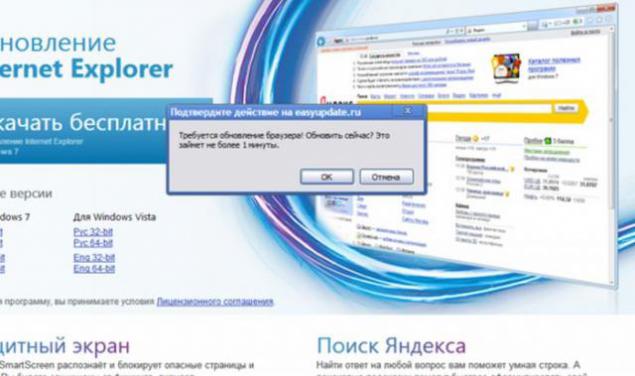
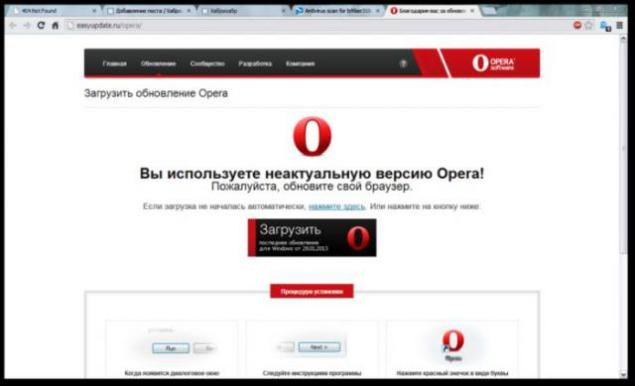
They have in common a very nice pop; vascript confirmation,
which starts to download the exe file, without even bothering to check,
which button the user clicked, OK or Cancel.
Virustotal
Thus, we have 5 samples
(links lead to the results of the scan files Virustotal):
chromesetup.exe, firefox-setup.exe, ie-setup-full.exe, opera_int_setup.exe and skypesetup.exe
opera_int_setup.exe and ie-setup-full.exe have not been scanned before me,
that is, the spread of infection was launched recently,
However, other files from antivirus reacted 8-9 46.
Kaspersky somehow the only one classified exe, as "not a virus»:
«Not-a-virus: HEUR: Downloader.Win32.LMN.a».
Perhaps this decision has positively impacted the digital signature, but it is better,
than a solution built into Windows antivirus from Microsoft,
that the samples did not see any threat at all.
For chromesetup.exe available information about the behavior, apparently
provided some of the anti-virus companies, including network activity:
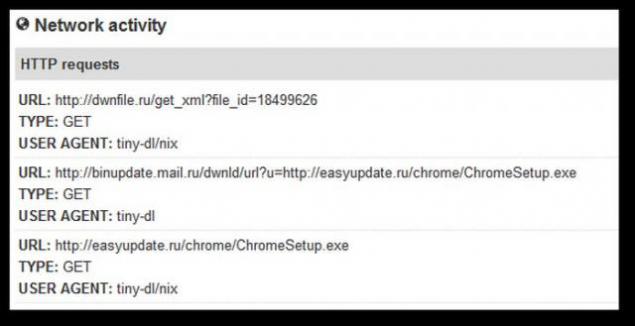
So, we have two strange domain and link to the subdomain Mail.ru,
take a closer look at them: easyupdate.ru recorded January 30, 2013
with hidden information about the owner (Private person), this service is available and free
the majority of Russian domain registrars. At the root of the site we were met by 404:
404 Not Found
The resource requested could not be found on this server!
Powered By LiteSpeed Web Server
LiteSpeed Technologies is not responsible for administration and contents of this web site!
The second link is obviously used the vulnerability of the type of URL redirect
one of the subdomains Mail.ru, however, apparently,
the vulnerability of already eliminated. Perhaps the attackers decided,
that such a reference is easier to pass through the firewall.
The domain is registered dwnfile.ru February 1, 2013 with concealed information about the owner.
Landing page text also contains links to the following domains:
uprgadotesbest.com - registered by December 26, 2012 through
PrivacyProtect.org and currently has the status «Locked»
uploadeasy.ru - the domain is not registered at all, seems to have forgotten
in the bustle of rolling out "in production" cybersquatters, flown!
All domains registered through Reg.ru.
In addition, the Trojan disables the registry proxy,
which clearly affect the operation of IE and Chrome,
Firefox and Opera have their own proxy settings.
Affiliate
Further, the link _http: //dwnfile.ru/get_xml? File_id = 18499626 returns
us the following XML content:
& lt; file & gt; & lt; dltype & gt; simple & lt; / dltype & gt; & lt; url & gt; & lt; / url & gt; & lt; referer & gt; profitraf1 & lt; / referer & gt; & lt; internet & gt; & lt; / internet & gt; profitraf4 & lt; mpcln & gt; & lt; / mpcln & gt; & lt; / file & gt;
Anyone looking at the contents of this simple, it is clear,
that we are dealing with another affiliate program on the so-called
"INSTALL" parameter guid - a unique identifier for the bot in the future
botnet and partner in this context - it's affiliate,
people registered in the affiliate program, received in her office
links to files for distribution and distribute these files to the best of his
corruption to give a certain percentage of the income owners of the affiliate program and botnet
from unsuspecting users. Googling ID profitraf1,
We go to the affiliate program itself: profitraf.ru
Registering only invites, but the first comer
Google came to invite and I got inside:
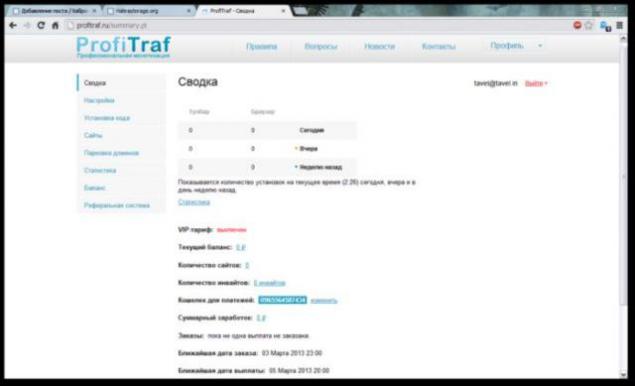
We met a nice design, statistics, balance and even referral system,
all very canonical. In the "Setting code" is written:
To work with the affiliate program you want to change any links to
downloadable content (mp3, document, video - absolutely any file) located on your site.
Links are changed so that instead of your domain to point to a special loader,
located on the domain profidownload.ru.
This reference specially prescribed initial link (that was previously on the site).
By clicking the user first starts the boot loader is loaded and,
who downloads a user's computer source file.
At the same time downloading the toolbar installed and a browser.
For the user, this is practically imperceptible.
So, you can connect your site to change it links to these and make a profit.
And here's another quote, this time from a huge,
215 pages, the topic of this forum on the largest affiliate webmasters in RuNet:
We offer an absolutely transparent, "white" salary scheme -
without SMS-subscriptions paid archives and other "gray" schemes.
We distribute the browser toolbar (add-in for browsers), the largest company
RuNet - Mail.Ru. Each site is rigorously moderated
and only after checking by our experts allowed to participate in the program.
And here I am, at last, it became clear where did the digital signature on Mail.ru Malvar,
Once a computer my mom.
The fact that this is the Malvar, no doubt, it is enough to study the results
examination of samples by antivirus companies.
And this infection can get very widespread, considering the chosen methods
disguise updates most popular
software for Windows.
The disappointing results of
I would like to note that I personally find very disappointing was the final
his home investigation itself corporation Mail.ru,
since the beginning, this option seemed to me most improbable.
Of course, even if this story will be made public,
officially shove the blame on the "unfair" partner, but,
In my opinion, a company that provides a digital signature
everyone you meet for the unauthorized downloading onto computers
unsuspecting users Trojan software,
is worthy of the title "botmaster" year. Where there is home-grown virus writers
without a certificate, a huge botnet, like Mail.ru,
they will never increase. And who knows, as the above mentioned corporation
decides to monetize their hapless users,
when she had things go worse than it is now.
Update March 12,
To date, no malicious domain is no longer resolves.
Perhaps this is due to the fact that this topic even in the sandbox was
roindeksirovan Google and began to show the extradition request «easyupdate.ru».
From
LLC Mail.Ru, which masquerades as an update of popular programs.
Be vigilant, comrades.
Many Internet users have noticed strange messages in a variety of applications that offer to install or upgrade version of the popular program.
Today I want to tell you about the banal update the Skype.
After confirmation by the user update from the infected source
downloaded and installed "update", but when he saw after the launch,
that the file is signed by the publisher somehow «LLC Mail.Ru», instead of Skype,
I advise you to immediately ban the execution of the task.
Read more about the fresh filling botnet scheme.
In most cases, after clicking on the "software update" comes redirect
to boot from the infected sites by type _http: // «any site name» / skype /,
looking something like this ...

"Your version of Skype, LLC, its support will end 04.03.2013,
then you will not be able to communicate by Skype »it is very frightening,
Riddle signature
So, first of all look at the file properties:

Strangely, only 74 KB, once is not enough even for web-installer.
Enjoying a digital signature, what is this «LLC Mail.Ru» is,
can someone again dragged through the legal entity Thawte similar name?

Strangely, the digital signature certificate is very similar to this from the Mail.Ru:

They have the same validity period of 02.07.2014 to 09.12.2011, but
in a digital signature has a signature Agent Mail.ru others:
Symantec Time Stamping Services Signer. All exe files are signed
on the fly before giving the browser to download,
This is evidenced by dynamically changing the time of signature file.
Total, we have three options:
1. This is a real digital signature Mail.ru, a private key from which
somehow stolen and now is used for signing Malvar
2. This is a real digital signature Mail.ru, which itself Mail.ru any reason
uses for signature Malvar
3. It is a fake digital signature Mail.ru, which is in any way
We were able to compromise (which is unlikely, since RSA 2048 bits)
Zaguglit source that is most often used by hackers - «easyupdate.ru»,
and did not find anything worthwhile to issue, I looked at all the links on demand site: easyupdate.ru
and found that, in addition to Skype, Landing are available for all popular browsers:




They have in common a very nice pop; vascript confirmation,
which starts to download the exe file, without even bothering to check,
which button the user clicked, OK or Cancel.
Virustotal
Thus, we have 5 samples
(links lead to the results of the scan files Virustotal):
chromesetup.exe, firefox-setup.exe, ie-setup-full.exe, opera_int_setup.exe and skypesetup.exe
opera_int_setup.exe and ie-setup-full.exe have not been scanned before me,
that is, the spread of infection was launched recently,
However, other files from antivirus reacted 8-9 46.
Kaspersky somehow the only one classified exe, as "not a virus»:
«Not-a-virus: HEUR: Downloader.Win32.LMN.a».
Perhaps this decision has positively impacted the digital signature, but it is better,
than a solution built into Windows antivirus from Microsoft,
that the samples did not see any threat at all.
For chromesetup.exe available information about the behavior, apparently
provided some of the anti-virus companies, including network activity:

So, we have two strange domain and link to the subdomain Mail.ru,
take a closer look at them: easyupdate.ru recorded January 30, 2013
with hidden information about the owner (Private person), this service is available and free
the majority of Russian domain registrars. At the root of the site we were met by 404:
404 Not Found
The resource requested could not be found on this server!
Powered By LiteSpeed Web Server
LiteSpeed Technologies is not responsible for administration and contents of this web site!
The second link is obviously used the vulnerability of the type of URL redirect
one of the subdomains Mail.ru, however, apparently,
the vulnerability of already eliminated. Perhaps the attackers decided,
that such a reference is easier to pass through the firewall.
The domain is registered dwnfile.ru February 1, 2013 with concealed information about the owner.
Landing page text also contains links to the following domains:
uprgadotesbest.com - registered by December 26, 2012 through
PrivacyProtect.org and currently has the status «Locked»
uploadeasy.ru - the domain is not registered at all, seems to have forgotten
in the bustle of rolling out "in production" cybersquatters, flown!
All domains registered through Reg.ru.
In addition, the Trojan disables the registry proxy,
which clearly affect the operation of IE and Chrome,
Firefox and Opera have their own proxy settings.
Affiliate
Further, the link _http: //dwnfile.ru/get_xml? File_id = 18499626 returns
us the following XML content:
& lt; file & gt; & lt; dltype & gt; simple & lt; / dltype & gt; & lt; url & gt; & lt; / url & gt; & lt; referer & gt; profitraf1 & lt; / referer & gt; & lt; internet & gt; & lt; / internet & gt; profitraf4 & lt; mpcln & gt; & lt; / mpcln & gt; & lt; / file & gt;
Anyone looking at the contents of this simple, it is clear,
that we are dealing with another affiliate program on the so-called
"INSTALL" parameter guid - a unique identifier for the bot in the future
botnet and partner in this context - it's affiliate,
people registered in the affiliate program, received in her office
links to files for distribution and distribute these files to the best of his
corruption to give a certain percentage of the income owners of the affiliate program and botnet
from unsuspecting users. Googling ID profitraf1,
We go to the affiliate program itself: profitraf.ru
Registering only invites, but the first comer
Google came to invite and I got inside:

We met a nice design, statistics, balance and even referral system,
all very canonical. In the "Setting code" is written:
To work with the affiliate program you want to change any links to
downloadable content (mp3, document, video - absolutely any file) located on your site.
Links are changed so that instead of your domain to point to a special loader,
located on the domain profidownload.ru.
This reference specially prescribed initial link (that was previously on the site).
By clicking the user first starts the boot loader is loaded and,
who downloads a user's computer source file.
At the same time downloading the toolbar installed and a browser.
For the user, this is practically imperceptible.
So, you can connect your site to change it links to these and make a profit.
And here's another quote, this time from a huge,
215 pages, the topic of this forum on the largest affiliate webmasters in RuNet:
We offer an absolutely transparent, "white" salary scheme -
without SMS-subscriptions paid archives and other "gray" schemes.
We distribute the browser toolbar (add-in for browsers), the largest company
RuNet - Mail.Ru. Each site is rigorously moderated
and only after checking by our experts allowed to participate in the program.
And here I am, at last, it became clear where did the digital signature on Mail.ru Malvar,
Once a computer my mom.
The fact that this is the Malvar, no doubt, it is enough to study the results
examination of samples by antivirus companies.
And this infection can get very widespread, considering the chosen methods
disguise updates most popular
software for Windows.
The disappointing results of
I would like to note that I personally find very disappointing was the final
his home investigation itself corporation Mail.ru,
since the beginning, this option seemed to me most improbable.
Of course, even if this story will be made public,
officially shove the blame on the "unfair" partner, but,
In my opinion, a company that provides a digital signature
everyone you meet for the unauthorized downloading onto computers
unsuspecting users Trojan software,
is worthy of the title "botmaster" year. Where there is home-grown virus writers
without a certificate, a huge botnet, like Mail.ru,
they will never increase. And who knows, as the above mentioned corporation
decides to monetize their hapless users,
when she had things go worse than it is now.
Update March 12,
To date, no malicious domain is no longer resolves.
Perhaps this is due to the fact that this topic even in the sandbox was
roindeksirovan Google and began to show the extradition request «easyupdate.ru».
From
Tags
See also
4 danger sign when choosing a partner, you will never have to ignore
Table for 20,000 rubles with his own hands
Mauritius. A paradise
Child Elements
Popular cheats on the Internet (13 photos)
Ustyurtnye expanses
How to shop at foreign online stores
Dangerous technology
Professions of the future: When we fly into space?
Mental viruses.